What is TTP in Cybersecurity? Tactics, Techniques, and Procedures
- -
- Time -

TTP or tactics, techniques, and procedures explain the threat actor’s behavior and provide a framework for why they execute a cyberattack. Hacktivists, amateur hackers, independent cybercriminals, clandestine organizations, and state-sponsored enemies are only a few examples of these actors.
Businesses can identify, assess, and take proactive measures to address security risks by knowing a cyberattack kill chain’s tactics, techniques, and procedures. Let’s understand what is TTP in cybersecurity through this article.
What is TTP in Cybersecurity?
Let’s understand what is TTP in cybersecurity. Cybersecurity professionals utilize tactics, techniques, and procedures, or TTPs. This term defines processes, behaviors, strategies, and actions a threat actor takes to create threats and engage in cyberattack activities.
TTP offers security people information about the how and why of cyber attack behaviors and helps them protect themselves.
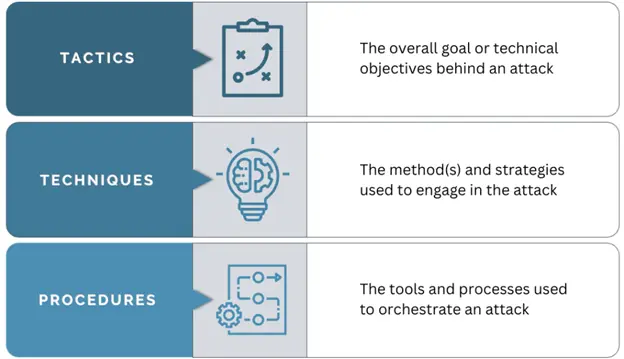
Tactics
It describes why or the technical objective of the threat actor performing the cyberattack. For example, the hacker’s aim may be to run malicious codes on the system or steal confidential data. A common tactic used by attackers is phishing. This involves sending fake messages or emails from legitimate sources to trick people into providing valuable information.
It can be an effective tactic as most people are unaware of phishing signs and can easily fall victim to such a practice.
Techniques
This describes the how of the cyberattack. Simply put, the methods the threat actor will use for attacking. For example, they may use brute force to access the accounts with encrypted or unknown passwords. There can be specific techniques with sub-techniques to explain how it happened.
To understand, let’s take the same brute-force example. Here, the attacker may start by guessing passwords to gain access or work on password cracking by using credentials of unrelated accounts. Other common ones are malware and ransomware. Malware is software created to harm a system through trojans, viruses, and other software.
But, a kind of malware called ransomware has the ability to encrypt your files and demand money in exchange for the decryption key. Such techniques can cause severe harm to any company and damage it significantly.
Procedures
This section describes how the attack happened in detail. It includes the practices and tools the attacker uses to accomplish its goal. In the same example of brute force, an attacker may use CrackMapExec to collect information from a targeted network for password cracking. Other procedures include botnets, a network of compromised systems controlled remotely to launch coordinated attacks or use exploit kits.
What is the Use of TTPs?
Cybersecurity professionals use TTPs to analyze the tactics, techniques, and procedures the threat actor uses for their counterintelligence efforts. These TTPs can help the professionals understand how the attack happened by knowing its complete framework.
TTPs assist researchers with incident response and threat mitigation, help define the threat’s severity, help researchers narrow their investigation route, and identify threat sources or attack vectors.
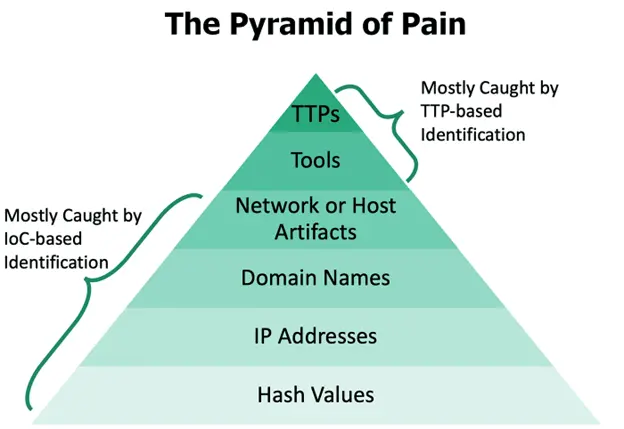
Security people also use these for threat activities and modeling. Moreover, this research goes beyond basic forensics. When researchers identify the attacker or the group, they also try to correlate their relationship with other attackers. Hence, it can also help eliminate the risk of any emerging threats and create threat countermeasures.
How to Use TTPs Against Cybercrime?
Knowing the different TTP combinations is an excellent way of dealing with cybercrime. You can simply follow the instructions laid down by several research bodies to create a response according to human verification and automated actions. For instance, the MITRE Attack Matrix can help cybersecurity professionals identify and address TTP.
It further defines how people can monitor IT activities, find abnormal behaviors linked with TTP, and prevent it from becoming a cyberattack. This matrix is excellent for intrusion detection and identifying the actors who plan these attacks.
Some other initiatives to deal with TTPs are:
- OWASP, an open web application security project, provides open research for common vulnerabilities and best practices that can impact web applications.
- CTA, cyber threat alliance – This is an agreement between many companies involved in knowledge sharing related to cybersecurity to create a safe environment.
Besides, technologies like UEBA, user and entity behavior analytics, and threat intelligence can help with data from research bodies. Behavioral analysis can be used to spot unusual activity, and threat intelligence feeds offer a wealth of information on threat actors and known attack patterns that can be utilized to spot TTPs in network traffic.
Since TTPs are essentially hacking activities, UEBA, which examines activity from the perspective of typical behavior, is a perfect match. Security solutions must swiftly identify and adjust to these new tactics since hackers keep creating and updating new TTPs. TTP data is essential to a security operations center’s (SOC) everyday operations since it helps security analysts stay one step ahead of attackers.
How Can TTPs Be Identified Using Behavioral Analytics?
TTP is analyzed to understand how the attack happened. It might be challenging to distinguish between malicious behavior and user-initiated routine network operations when digital evidence matching a TTP is present. For instance, all analysts know how attackers maliciously use account creation, remote desktop access, or screen sharing.
However, these tasks are performed daily by the IT department with a legitimate intent. Therefore, the SOC team must have tools to identify whether it is a regular or malicious activity and raise an alarm if it’s the latter. Otherwise, the system will generate more false positives and burden the security teams.
Hence, behavioral analytics can help as it uses machine learning to track and understand the behavior of users and assets. It also creates a behavioral baseline and quickly determines deviations from the usual activities to detect accurate malicious TTPs.
Different TTP Knowledge Bases
We already have some research bodies above that share information and knowledge about the various TTPs and their best practices. Besides those, you can also find information related to TTP through the below knowledge platforms:
#1. The Open/Web Source
You can find a lot of information on TTP on the internet. This data can be collected and used for threat intelligence. For example, you can use the web to understand the techniques for stealing credentials, such as passwords and accounts.
#2. Darknets or Honeypots
These can be used to track real-life exploit activities. Honeypot data can help you find security holes and vulnerabilities to strengthen your controls. They help spot malware and ransomware activities as well. Cybercriminals publish stolen info on darknets. They can be used to monitor data that hackers are willing to sell.
#3. Telemetry
This data can be gathered from systems to analyze how they are operating. For instance, you can collect telemetry information to understand the traffic generated by the system and the traffic it accepts. It can provide information on whether or not the system was compromised and the tactics used for it.
#4. Malware Processing
Malware analysis is an excellent way to understand a malware attack’s potential impact. It can also help identify behaviors that may be used in the future, such as accessing a particular port, domain, or network. This information makes it easier to track adversary behaviors and identify security gaps.
What Does TTP Mean for SMBs?
SMBs are small enterprises with less staff to understand TTPs. Hence, these companies must prepare for the worst and hope for the best.
Certain best practices mentioned below can be implemented to prevent this.
- If you encounter any possible attack, try to understand whether your IT team has ever faced something similar.
- Use this knowledge and information to prepare appropriate actions.
- Further, it can be used to identify possible attackers.
- This information can also help you identify the systems that are more prone to these attacks.
- Protect your company through regular monitoring, mitigation, and neutralization.
How to Use TTPs to Drive Cybersecurity Strategy?
A complete understanding of TTP can strengthen any organization’s overall security system and positioning. There are several ways of doing so, some of which are mentioned below:
Tailored Security Measures
If companies know specific TTPs, they can design security solutions that may directly address any relevant threat they face. This includes implementing advanced endpoint detection for malware or enforcing robust access control against some known cyberattack techniques.
Enhanced Threat Intelligence
Companies that understand the attacker’s behavior stay ahead of current and future threat intelligence. Using this information, cybersecurity teams can forecast any potential attacks and modify their defense systems accordingly.
Proactive Defense Posture
TTP analysis can also help identify immediate vulnerabilities and emerging cyber-attack threats, facilitating a proactive transition from reactive fighting to risk management. This makes companies more equipped to prevent incidents instead of responding after they have happened.
Focused Training and Awareness Program
When companies have a vast knowledge base of how the attackers may attack, they can create target-based training programs for everyone. Every employee across all levels can attend these training sessions, from end users to IT people responsible for recognizing any signs of compromised attacks.
Companies can even tie up with training providers, such as CCSLA, to offer cybersecurity courses to their employees. This can help them understand and prepare for any possible attack.
Optimized Incident Response Plan
In-depth scenarios that mirror real-world attacker protocols offer vital frameworks for incident response exercises, guaranteeing that plans are strong, current, and functional in the case of cyberattacks.
Organizations acquire deeper situational awareness that influences all aspects of their operations, from daily operational choices to strategic planning to policy-making and individual user behaviors, by incorporating knowledge of adversaries’ TTPs into their larger cybersecurity framework.
In the end, when it comes to safeguarding sensitive data assets, businesses can integrate resilience into the very fabric of their company culture.
Examples of TTPs
Here are some examples of TTPs and how they relate to each other:
Example 1
- Tactics – initial access
- Technique – spear phishing email
- Procedure – The file types that attackers frequently attach, the exact email templates they utilize, and the social engineering techniques they employ.
Example 2
- Tactics – credential access
- Technique – credential dumping
- Procedure – The instruments, instructions, and methods applied to hash and password extraction.
Conclusion
Any organization looking to enhance cybersecurity must understand tactics, techniques, or procedures (TTPs) in detail. This will help protect your team from current attacks and prepare them to identify and defend themselves from future attacks. One of the best ways to understand and enhance knowledge is by undertaking TTP or other cybersecurity-related courses.
CCLSA is one of the pioneering platforms offering various cybersecurity courses and training programs to help individuals or companies enhance their skills and knowledge. You can check their page to find more relevant skills development courses.
FAQs
In cybersecurity, TTP stands for Tactics, Techniques, and Procedures. These are used to describe the behavior and methods of cyber attackers in detail, encompassing how they plan and conduct their attacks (tactics), the specific tools and methods they use (techniques), and the exact processes they follow (procedures).
TTPs are used to identify, assess, and defend against cyber threats. By understanding the specific tactics, techniques, and procedures used by attackers, cybersecurity professionals can better anticipate and mitigate potential security breaches, adapting their defense mechanisms to more effectively counter and neutralize threats.
During a cybersecurity incident, analysts might identify that attackers used spear-phishing emails (technique) as a method to deliver malware. The emails, crafted to appear as if they came from a trusted source, contained malicious attachments that, when opened, executed malware that stole data (procedure). The tactic behind this approach could be to gain unauthorized access to sensitive information.
Studying TTPs is crucial as it helps in building a comprehensive understanding of threat actors and their evolving behaviors. This knowledge is vital for developing effective security strategies, improving threat detection capabilities, and implementing robust defensive measures tailored to the specific methods used by attackers.
Organizations use TTPs to enhance their security posture by incorporating this intelligence into their security systems and protocols. This includes training employees to recognize specific techniques and procedures, updating and patching systems to defend against known exploits, and simulating attacks to test the effectiveness of current security measures.
Resources such as MITRE ATT&CK framework provide a detailed and continuously updated database of threat actor TTPs. Cybersecurity training programs, professional workshops, and threat intelligence services also offer insights into identifying and mitigating based on TTP analysis.
TTPs evolve as attackers adapt to new security measures and exploit emerging vulnerabilities. Organizations can keep up by continuously monitoring for new threats, participating in cybersecurity communities for shared intelligence, and utilizing advanced threat detection and response technologies that adapt to changing attack methodologies.
Machine learning plays a significant role in identifying TTPs by analyzing large volumes of security data to detect patterns and anomalies that may indicate known or emerging threats. These systems can learn from new data, improving their accuracy over time in identifying sophisticated attack strategies.
Businesses should integrate TTP analysis into their cybersecurity strategies by regularly updating their threat intelligence, conducting security audits based on recent TTP discoveries, and training their security teams to recognize and respond to specific tactics, techniques, and procedures used by cyber attackers.






