What is Spillage in Cybersecurity? Definition, Examples & Prevention
- -
- Time -

Spillage in cybersecurity is a concerning issue that refers to the unintentional or deliberate exposure of sensitive data or information to unauthorized entities. Sensitive information getting into the wrong hands due to spillage can negatively impact individuals as well as organizations. That is why getting educated in cybersecurity is really essential.
In this article, we will comprehensively understand the concept of spillage, how it occurs, examples of spillage incidents and important prevention techniques.
Statistics from a 2024 survey revealed that 78% of companies worldwide rely on up to 10 different solutions for data security, yet many organizations continue to face security incidents, underscoring ongoing risks. These statistics highlight the critical nature of preventing spillage and the broader importance of data protection.
Definition of Spillage
As per the National Security Agency, the term ‘data spill’ refers to the transmission of classified or sensitive information to unaccredited or unauthorized systems, persons, applications or media.
Such transfers generally arise due to improper management of compartments, release controls, personal data or proprietary information rather than malice or criminal behavior. Important confidential information ‘spills’ from secured environments like encrypted databases to unsecured locations like emails in public spaces.
Read more: Is Cybersecurity A Good Career? Pros and Cons
How Spillage Occurs?
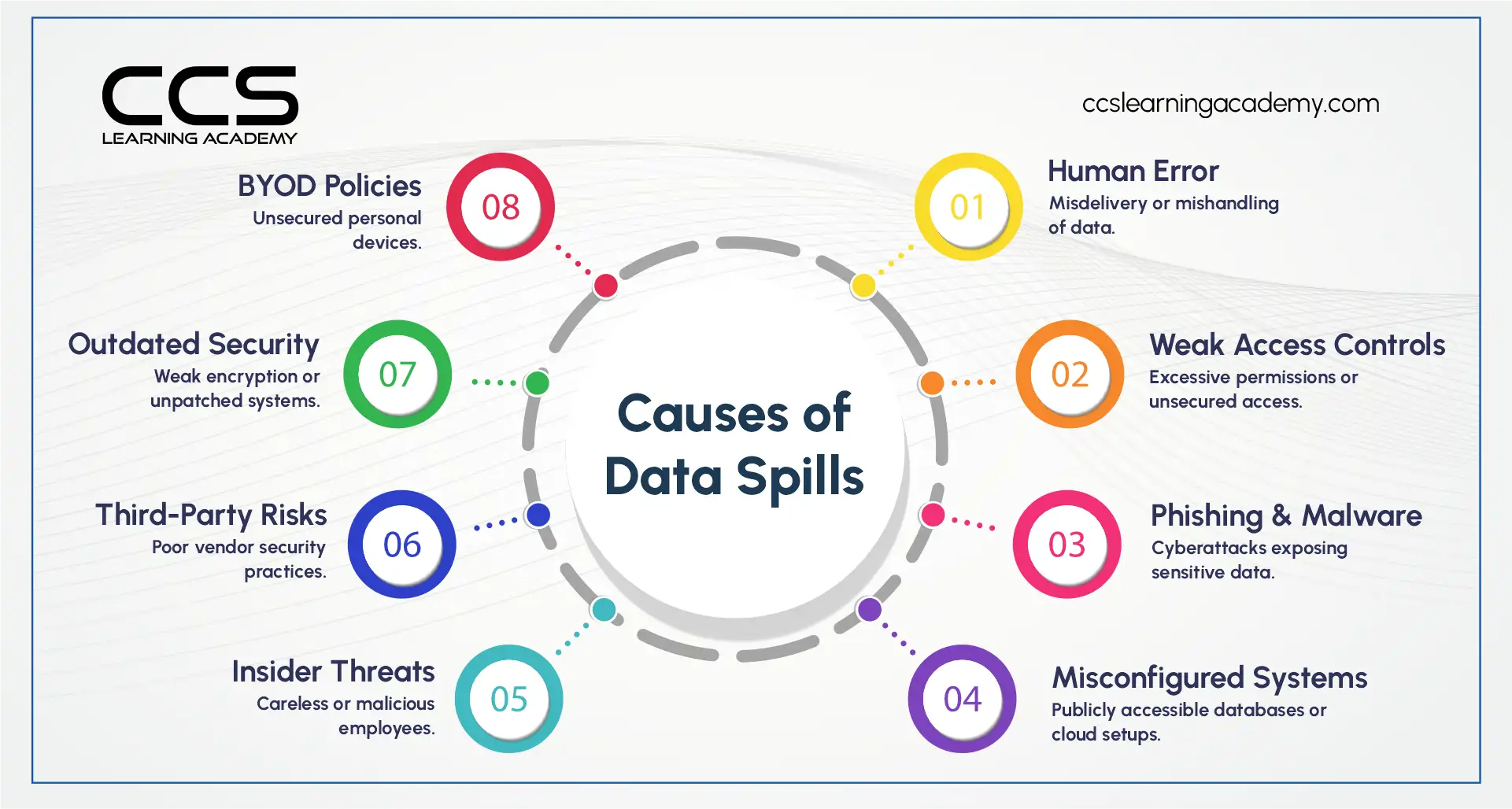
Spillage can occur through both deliberate and unintentional means. Sensitive data finds its way to unintended parties when proper security measures and protocols are not followed. Let us examine some of the common ways spillage takes place.
Weak Security Controls
Outdated software, insecure firewall configurations, and weak passwords are some of the security weaknesses exploited by malicious actors to cause spillage. When systems and networks are not properly secured, it becomes easy for hackers to break in and access sensitive information stored within.
Many organizations do not practice rigorous patch management and fail to promptly update their software applications. This leaves known vulnerabilities unpatched for a long period of time. Hackers actively scan networks to discover such security holes and leverage them to infiltrate systems. Once in, they can easily exfiltrate valuable data like customer records, intellectual property, financial records and more.
Similarly, improperly configured firewalls do not effectively restrict inbound/outbound network traffic as intended. With the ability to freely communicate on the web, hackers can perform reconnaissance, launch additional attacks and extract sensitive files from within the breached environments.
Furthermore, 84% of companies use cloud sync services, which, while useful for collaboration, are not true replacements for dedicated backup solutions. In fact, cloud providers suffered over 500 hours of downtime in aggregate in 2022, increasing the risk of data spillage.
Cyber Attacks
Sophisticated cyber attacks are deliberately planned and executed by motivated threat actors to cause spillage through no fault of the target. Malware infections, ransomware strikes and data breaches are some such attacks.
Malicious software like viruses, trojans and worms are designed to infiltrate end-user devices and spread internally within the network. Upon gaining a foothold, they can covertly extract valuable information from affected systems. This extracted data is either directly sent to command and control centers or temporarily stored for future exfiltration.
Ransomware works by encrypting important files and demanding ransom payments in cryptocurrency for the decryption key. Even if paid, there are no guarantees the threat actors will not retain data stolen prior to encryption. Sensitive documents, databases and other files get encrypted during such attacks, potentially locking out legitimate access.
Large scale data breaches remain a serious threat where outsider attacks or insiders with malicious intent compromise databases storing personal records of customers and employees. The stolen personal details often end up being published online or sold illegally on the dark web, causing widespread spillage.
System Vulnerabilities
Unguarded vulnerabilities are openings routinely scanned for and targeted by cyber criminals. When threat intelligence reveals flaws in commonly used software or devices, threats actors write exploits to take advantage. Unpatched systems expose such vulnerabilities, enabling spillage.
Outdated systems running legacy OS and applications split security patches. Known security issues in such outdated platforms get leveraged by attackers. Had patches been applied, a spike in exploits targeting publicly disclosed security holes could be avoided.
Misconfiguration of servers, databases and other infrastructure elements leave sensitive data unintentionally exposed. Improper access restrictions, unencrypted channels and incorrectly configured firewall policies result in spillage.
Improper File Sharing
Human errors where private information is shared outside official communication channels is a major cause of unintended spillage. Failure to properly classify, label and handle sensitive content while collaborating increases chances of exposure.
Mistakes happen when sending documents as email attachments to incorrect recipients. Sensitive documents containing personal identifiers, trade secrets or financials end up in the wrong hands, violating privacy and confidentiality.
Cloud collaboration portals and file sharing services see frequent mistakes. Uploading private data to public folders or shared links reaches unintended parties. Although not malicious, such errors result in spillage impacting many.
Lost or Stolen Devices
Portable digital devices like laptops and smartphones now process an immense amount of sensitive institutional data. However, physical loss of control over such devices puts that data at risk of theft or accidental exposure.
Laptops stolen during travel or break-ins provide direct access to unauthorized entities. Data on lost or stolen smartphones and tablets also becomes vulnerable if encryption and remote wiping is not enforced. Lack of endpoint protection on devices taken outside premises can lead to uncontrolled spillage.
Careless handling, failing to encrypt storage or transmit data securely from mobile endpoints increases chances of it unintentionally falling into wrong hands. Even after disposal, unencrypted drives sold for reuse may still contain recoverable remnants of private files, causing spillage.
Proper security controls, vigilance against cyber attacks and staff training can help reduce spillage occurring through these avenues. A multilayered approach is required to systematically tackle different sources of unauthorized information dissemination.
Read more: CISA vs CISM vs CRISC: Which is the Best Cybersecurity Certification?
Examples of Spillage
Some common examples of spillage incidents include:
Emailing Medical Records
A common example of data spillage occurs when hospital staff accidentally emails a patient’s confidential medical records to the wrong person due to human error. This type of spillage happens when an employee is accessing and transmitting protected health information but fails to verify the intended recipient of the email. Perhaps they mistype the email address or attach the wrong document. Since medical records contain sensitive details about a person’s health and treatment, accidental disclosure can compromise patient privacy and trust in the healthcare system.
Posting Passwords Publicly
Another example involves an employee accidentally posting organizational passwords on a public forum or social media platform, leading to a spillage. Staff may share credentials while discussing work issues online without realizing their mistake.
Cybercriminals could then access those passwords to infiltrate the company’s systems and steal confidential data. Posting login information exposes it to unauthorized access, enabling data theft and breaches. Employees must understand the risks of discussing security details where outsiders may see them.
Leaving Laptop Unattended
Data spillage can also arise when a user leaves their laptop unattended in a public space like a cafe or airport lounge, exposing any sensitive data visible on the screen.
With the laptop unlocked but unattended, bystanders may be able to view and even copy financial records, proprietary information, client lists or other confidential files right off the display. Portable devices must always be physically secured even for short durations to prevent inadvertent data leakage from prying eyes.
Misconfigured Cloud Storage
Incorrect access controls or configurations on cloud storage accounts where sensitive files are saved can also result in data spillage. When users upload protected documents and fail to apply proper sharing restrictions, unauthorized parties may access that information depending on the storage platform’s default viewability settings.
Similarly, file synchronization causes remote or public access on multiple unsecured devices. Organizations need configuration management policies for cloud assets to avoid spillage from misconfigured services.
Responding to Phishing
Users falling for socially engineered phishing scams is another common source of spillage when they download malicious attachments or reveal credentials. Deceptive emails try fooling recipients into providing private access codes or installing malware under false pretenses.
Once obtained, credentials enable threat actors to laterally move within systems to steal records. Repeated phishing awareness training helps employees identify and handle such ploys safely without inadvertent data loss.
Read more: Top 15 Cybersecurity Best Practices to Prevent Cyber-Attacks.
Effects of Spillage

Data spillage can have detrimental consequences for individuals as well as organizations:
Privacy and Security Risks from Exposed Personal Information
When personal information like names, addresses, social security numbers or financial information is spilled, it puts individuals at risk. Criminals could use spilled personal details to commit identity theft.
They might open accounts or secure loans in someone else’s name. Individuals would have to spend a lot of time and money repairing damage done to their credit and good name. The stress of a spilled identity can impact someone’s mental and financial well-being.
Financial and Legal Costs of Remediation and Fines
Cleaning up after a spillage is costly. Companies have to spend on technologies and labor to identify what was spilled, plug the holes that caused it and clean up after. Notification and recovery comes at high postage and call center costs if many people are impacted.
Regulators can impose hefty fines if laws were broken during a spillage. When individuals sue for damages to their lives, companies must pay expensive legal fees to defend themselves even if they win in court. The costs of remediation and potential litigation eats into company profits.
Operational Disruption and Financial Losses
When spillage takes place, companies may have to temporarily stop certain services while the impact is investigated and recovery carried out. This could lead to lost business, customers and money if the disruption drags on. If trade secrets or financials were spilled, it may lose the company competitive advantages and inventories it relied on.
Data thieves could also use spilled banking details or customer lists to directly defraud a company. The operational disruptions and out-of-pocket losses further impact a business’s bottom line.
Brand and Reputational Damage
News of a data spillage travels fast online nowadays. Customers quickly lose trust in companies that cannot protect their sensitive data. Brand reputation, a valuable intangible asset, takes a major hit in the court of public opinion.
Future customers may choose competitors perceived to be more reliable. Existing customers also jump ship due to breach anxiety. The long-term brand perception hit and loss of loyal customers has considerable monetary impact.
Competitive Threats from Stolen Trade Secrets
If a company’s research, formulas, strategies or plans are among the spilled information, competitors could unfairly utilize them without cost. The victim company loses advantages when it invests resources developing.
Stolen unique capabilities help opponents to directly compete effectively. They may surpass the victim company using its own stolen innovations and ideas. The loss of competitive edge poses a major threat to the company’s prosperity and market survival in the long run.
Read more: Top 11 High-Demand Cybersecurity Jobs Without a Degree.
Spillage Prevention

To prevent spillage, companies must implement a robust cybersecurity control framework consisting of:
Access Controls
Role-based access to data is essential to prevent unauthorized access and potential spillage. Only granting employees access to the specific resources required for their roles follows the principle of least privilege.
Implementing multi-factor authentication for accessing sensitive systems and data also makes unauthorized access more difficult. Audit logs of all access attempts should be regularly reviewed to detect any anomalous access patterns.
Encryption
Encrypting data both at rest and in transit is a critical line of defense against spillage. Data spilled after being encrypted is unusable without the encryption keys.
Setting up whole disk, file-level and in-transit encryption prevents unintended exposure even if endpoints or servers are compromised. Providing employees encryption guidance and tools helps safeguard sensitive information on removable media and laptops.
Employee Training
An ongoing security awareness program educates employees about secure information handling practices. Training covers classification and labeling of sensitive data, lock screen policies, avoidance of unsecured public networks and removable media.
Recognition of social engineering threats via phishing emails or malicious websites is also addressed. Refresher sessions ensure policies are properly understood and prevent lapses from becoming security risks or potential spillage events.
Secure Remote Working
As more staff work remotely, strong controls are required. Multi-factor VPN authentication eliminates password-only access to internal networks from unsecure locations. Monitoring VPN activity helps detect anomalous logins.
Controls are also placed on downloading data and use of personal devices for work to avoid information spillage.
Incident Response Planning
A predefined spillage response plan with clear roles and procedures ensures swift containment to limit damage. Designated teams are trained to determine the scope and root cause through forensic investigation if spillage occurs.
All at-risk systems are isolated, affected users notified, and remedial actions instigated to close vulnerabilities exploited. Lessons learnt feed back into enhanced prevention controls.
Monitoring and Detection
Deployment of tools like SIEM, DNP, firewalls and endpoint detection provides network-wide visibility. Algorithms and rules profile typical user and entity behavior and system transfers to flag anomalies for review.
Any unauthorized data movement attempts or policy violations are blocked in real-time. Sensitive information identifiers also aid detection of any potential spillage incidents.
Vulnerability Management
Regular security audits assess weaknesses before being exploited for spillage. All systems, applications, configurations and access controls are checked for vulnerabilities and misconfigurations.
Vulnerability databases are also regularly updated to identify any newly reported security holes. A risk-based patch management program promptly installs software and firmware updates to close vulnerabilities. Penetration testing further identifies ways to strengthen defenses.
Adopting such measures across people, processes and technologies safeguards sensitive information from unintended exposure.
Read more: CISSP vs. Security+: Which is the Best Cybersecurity Certification?
Conclusion
In today’s digital world, with rising remote working trends and sophisticated cyber-attacks, the risks of spillage are increasing. Focusing on prevention is important for organizations as well as individuals to avoid the detrimental outcomes of spillage. Implementing robust cybersecurity protocols, employee training along with continuous monitoring and improvement can help mitigate this critical threat.
CCS Learning Academy offers a comprehensive range of cybersecurity courses designed to equip professionals with the skills needed to prevent and respond to these evolving threats. With expert-led courses and continuous skill development, CCS Learning Academy helps you stay ahead of cyber risks while effectively safeguarding critical assets and information.
Investing in cybersecurity education is one of the most powerful steps you can take to protect your organization against spillage and the costly consequences of data breaches.
FAQ
A: Data spillage typically occurs when sensitive information is unintentionally exposed, shared, or transferred to an unauthorized system, often due to human error, system flaws, or security breaches.
A: Examples include accidental emails with sensitive attachments, misconfigured cloud storage, or employees mistakenly sharing confidential information on unsecured platforms.
A: Organizations can prevent spillage by implementing robust security policies, using encryption, conducting regular security audits, and training employees on data handling best practices.
A: Strong access control limits who can view, modify, or transfer sensitive information, reducing the chances of accidental exposure and ensuring only authorized users can access critical data.
A: Data spillage can lead to financial loss, legal consequences, damage to reputation, and compromise of sensitive information, all of which can severely affect an organization’s operations and trust.
A: Encryption ensures that even if data is accidentally exposed or intercepted, it remains unreadable without the appropriate decryption key, adding an extra layer of protection.
A: Tools like Data Loss Prevention (DLP) software, secure file-sharing platforms, and real-time monitoring solutions help detect unauthorized access and prevent accidental data exposure.
A: Recovery from a spillage incident involves identifying the exposed data, mitigating any further risks, notifying affected parties, and implementing corrective actions to prevent recurrence.
A: Regulatory frameworks like GDPR, HIPAA, and CCPA mandate strict measures for data protection and impose penalties for data spillage, encouraging organizations to adopt preventive strategies.
A: Failing to address spillage can result in financial penalties, legal action, compromised customer trust, and significant operational disruptions.






