What is Skimming in Cyber Security? Examples, Risks & Prevention
- -
- Time -

As technology plays an increasingly central role in our lives, it has also opened new avenues for cybercriminals to prey on unsuspecting users. One such cybercrime is skimming – the act of stealing individuals’ financial information to commit fraud.
In this detailed guide, we delve into what skimming entails, how it works, common examples, associated risks, and key steps everyone can take to safeguard themselves.
What is Skimming in Cyber Security?
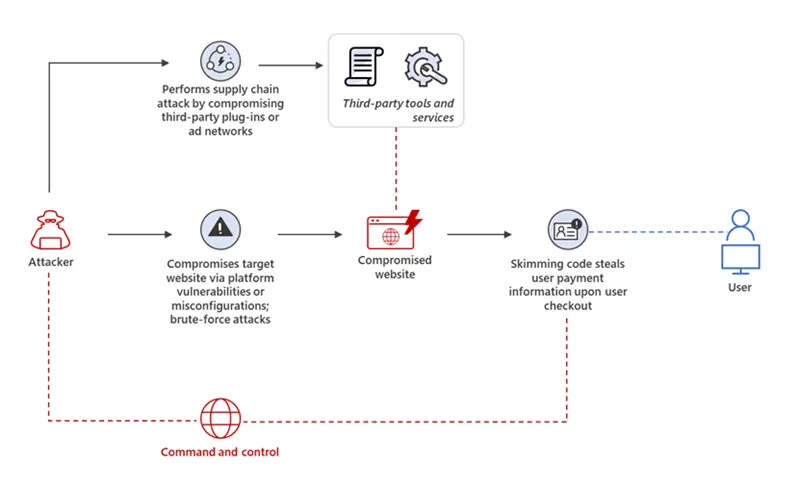
Fundamentally, skimming refers to the covert copying of payment card details and personally identifiable information (PII) without the cardholder’s knowledge or consent. The term originates from how skimming devices physically work to clone magnetic strips on payment cards. In a cyber context, it involves harvesting sensitive financial data through deceitful means such as phishing scams, malware infection, or tampering with point-of-sale (POS) systems.
The overarching goal of any skimming operation is to infiltrate an individual’s financial accounts by exploiting weaknesses in security protocols. Once stolen credentials fall into the wrong hands, cybercriminals can freely spend money, commit identity theft, or sell the information on dark web markets. As digital transactions pick up the pace globally, so have attempts to pilfer financial data through complex online schemes.
Common Skimming Methods
While technology continues evolving skimming tactics, some long-standing techniques persist:
Physical skimming
Perhaps the oldest skimming method still actively leveraged today involves physically tampering with cash machines and point-of-sale terminals to covertly duplicate card information. Referred to as physical skimming, this entails sneakily affixing concealed card readers or miniature cameras to existing infrastructure in order to either swipe or photograph payment details from unwitting victims.
Typically targeting high-traffic areas devoid of careful oversight, perpetrators have long zeroed in on setting up these sly devices at gas stations, restaurants, and especially ATM machines frequented by many patrons in a day. The illicit duplicated magnetic stripe data can then be cloned onto counterfeit cards for weeks of fraudulent withdrawals and purchases before discovery.
E-skimming
While physical skimming remains a go-to tactic for its low-tech convenience, cybercriminals have dramatically scaled up their abilities to remotely pilfer payment records through the infiltration of online networks. Referred to as e-skimming or web skimming, this burgeoning threat involves maliciously injecting malware into the websites and applications run by legitimate merchants. This could entail compromising vulnerable servers to secretly download agent payloads or modifying website codebases to bury sneaky JavaScripts.
Once infected, the sites function normally for customers but have been weaponized to covertly siphon card details entered during online checkouts. The stolen information gets relayed back to attackers in real-time without ever arousing suspicion at the moment. E-skimming presents an especially pernicious menace because victimization can happen remotely from anywhere in the world with only an internet connection needed.
Phishing
Another thriving skimming vector involves tricking victims into self-disclosure of sensitive credentials through impersonation, commonly known as phishing. This deceitful plot relies on spreading misleading messages that socially engineer targets into clicking malicious links or opening harmful file attachments.
Often posing as notices from banks, merchants, or government agencies, phishing communications frequently warn of account issues requiring login verifications or request form filling on look-alike spoof pages. Once lured, the dummy sites and rogue programs seamlessly record whatever identifiers and passwords get entered, handing thieves all they need for large-scale takeovers and thefts. While phishing seems a crude tactic, its low-tech nature also means evasion proves easy, allowing endless refining and reattempting until successful hits occur.
Keylogging malware
To further compound matters, skimmers have taken to subverting users’ trust in even the devices they perceive as most secure, like personal computers and smartphones. This involves sneaking malware payloads onto systems under the guise of useful programs or interesting online content. Dubbed keylogging malware, these spyware suites clandestinely run in the background, logging every keystroke tapped without ever raising the alarm.
As people routinely save banking login credentials and make bill payments through these very endpoints, cybercriminals have eagerly embraced keyloggers as a means of passively waiting to extract banking account numbers, usernames, passwords, and even one-time codes from infected devices over weeks or months. Once amassed, this abundant stolen data gets exploited in waves of account takeovers and fraudulent transactions.
Wi-Fi skimming
Advancing alongside evolving connectivity, wireless has emerged as another avenue of attack in what is referred to as Wi-Fi skimming. This involves clandestinely setting up rogue wireless hotspots that masquerade as legitimate public networks, enticing people into connecting without a second thought. Yet, in reality, these fake wireless signals have been designed solely for the purpose of intercepting transmitted web traffic and extracting unencrypted sensitive details from unsuspecting connections.
People logging into online bank accounts, making mobile wallet payments, and transferring funds on these poisoned networks see all their actions and credentials vacuumed up in real-time. The resultant stolen information can then be exploited at leisure by the cybercriminals behind these covert Wi-Fi traps.
ATM skimming
Alongside evolving remote techniques, fraudsters still find success through old faithful tactics that remain as effective as ever with physical access. Foremost among these is ATM skimming, which involves sneakily mounting tiny card-copying mechanisms directly within or alongside existing cash machine card slots. Appearing fully integrated, these concealed cloning devices surreptitiously duplicate the magnetic stripe data from each payment card inserted during transactions. The illicit card copies then get created off-site for extensive testing before full counterfeit duplicates get mass-produced and encoded to cash out from compromised accounts.
Criminals favor targeting high-volume ATMs in less supervised locations for their skimming antics, counting on going unnoticed as they invisibly rake in copied card credentials from countless oblivious victims each day.
POS system tampering
In addition, cyber crooks have taken to tampering with retailers’ entire payment systems in what is referred to as compromised POS terminals. This involves either physically accessing point-of-sale equipment like cash registers to install rogue hardware or malware or remotely breaking into vulnerable back-end networks and controlling numerous locations simultaneously. Once in, thieves can selectively scrape transaction histories, backdoor administrator tools for continued access, and even rewrite firmware on compromised terminals.
POS tampering opens the floodgates for harvesting massive caches of stored card numbers as well as hijacking live authorizations right at the source. Such all-encompassing breaches can drain millions from thousands of accounts before victims even realize skimming has occurred from stores they frequented.
Considering how each of these long-running techniques persists in constantly evolving forms that are difficult to preempt, vigilance remains paramount in thwarting skimming’s damaging impact. As new attacks arise copying old strategies through technical tweaks, the human elements exploited stay relatively unchanged – enticing people into parting with sensitive info or accessing networks surreptitiously modified without their knowledge.
Financial and Reputational Risks
For individuals, falling prey to skimming means imminent risks like unauthorized charges, identity theft, and long-term credit damage. Beyond the immediate monetary losses, victims also suffer emotional distress and headaches recovering compromised accounts.
Businesses endure sizable operational and compliance costs by investigating attacks, notifying impacted customers, providing credit monitoring solutions, and patching security loopholes. Payment processors further shoulder liability risks under compliance rules like PCI DSS.
Reputational harm also significantly affects companies as data breaches spark customer distrust and negative media attention. This blows a dent in brand value while disgruntled users potentially abandon compromised services.
From a wider societal lens, skimming translates to economic losses amounting to billions annually. It further subsidizes other cybercrimes like human trafficking, drug peddling, and money laundering, implicating national interests. Theft of sensitive identity markers especially endangers privacy and national security.
Preventing Skimming Attacks
While cybercriminals continue devising new schemes to steal personal and financial information, both individuals and businesses can take proactive steps to thwart many skimming attempts. Criminals exploiting human vulnerabilities through social engineering remain a challenge. However, layering basic security fundamentals with smart security practices significantly raises the bar against opportunistic skimmers.
For Individuals
Use Chip-Enabled Cards
When possible, opt for chip-enabled credit and debit cards instead of swiping the magnetic stripe. Referred to as EMV or chip-and-PIN technology, the embedded microchips generate unique one-time codes for each transaction. This helps reduce the risk of card data being copied and used for fraudulent purchases. While chip technology is still being developed in some regions, asking merchants if they accept chips makes it the default payment method.
Review Bank Statements Regularly
Carefully examining transaction records each month for unauthorized or erroneous charges is key. Any discrepancies should be immediately reported to the issuing bank to halt losses and initiate fraud investigations. Banks may reimburse losses from invalid charges, but acting fast maximizes financial protection and limits damage. Statement scrutiny also encourages more diligent practices by financial institutions to curb repeated breaches.
Use Strong, Unique Passwords
Accessing online bank accounts requires robust, unique credentials for each service. Weak passwords consisting of personal details that are easily guessed or cracked should be avoided. Consider a passphrase of random words instead of just numbers and symbols. Also, two-factor authentication is available as an extra layer of protection against account takeovers, even if passwords get compromised. Regularly changing passwords is also advised to thwart efforts of credential-stuffing.
Exercise Online Caution
Be wary of unsolicited emails, texts, or phone calls asking for personal information like account numbers, login IDs, and PINs. Legitimate organizations will never request sensitive details through unofficial channels. Phishing and vishing attempts to social engineer victims through deceit should immediately be deleted or hung up on. Also, avoid public Wi-Fi for financial transactions unless a trusted VPN is used to encrypt communications.
Use Updated Anti-Malware Tools
Installing and consistently updating reputable anti-virus, anti-spyware, and firewall software on all internet-connected devices forms the foundation of online safety. Malware deployed through infected websites or email attachments remains a primary infection vector for banking Trojans and keyloggers. Keeping security suites up-to-date with the latest definitions minimizes risks while diligently applying patches that also plug vulnerabilities.
For Businesses
Install Anti-Tampering Protection
Outside-facing payment terminals, especially older ones that do not support EMV, should have measures to detect tampering or implanting of skimmers. Enclosure locks, tamper-evident seals, and sensors can help spot compromised devices and reduce exposure windows. Surveillance cameras also aid investigations, while visible security tools serve as a deterrent against would-be fraudsters.
Deploy EMV-Certified Readers
Accepting chip-based transactions at points-of-sale should be the priority by upgrading older magnetic stripe-only terminals. Going further with contactless payment acceptance opens the business to consumers preferring tap-and-pay convenience. Certified EMV implementation not only future-proofs compliance but also shifts fraud liability and pressures financial institutions to invest in solutions that curb criminal proceeds from stolen card data.
Regularly Monitor Networks
Network-level intrusion detection and asset inventory systems keep a close watch for any rogue devices or applications connected without authorization. The discovery of anomalous hardware, such as additional wireless access points or the presence of malware, gets flagged for swift remediation to block the exfiltration of stored payment data. System images also aid forensic investigations of past compromises.
Segregate Payment Systems
Isolating payment systems and cardholder data environments from general business networks limits the attack surface and potential fallout from vulnerabilities elsewhere. Strict change control policies further govern configurations to Payment Card Industry Data Security Standard (PCI DSS) mandated specifications. Segmentation, when properly implemented and audited, strengthens overall security posture.
Conduct Risk Assessments
Regular vulnerability assessments, network scans, and penetration tests uncover weak spots for remediation before criminals discover them. Policy reviews ensure compliance with evolving security guidelines and reevaluate responses in light of emerging threats. Training also equips employees to identify social engineering ploys and report irregularities. Audits confirm existing safeguards continue addressing requirement changes effectively over time.
Partner for Guidance
Working with experienced PCI Qualified Security Assessors helps align programs according to best practices. Their expertise proves invaluable to methodically close compliance gaps, improve maturity levels over time, and prepare for upcoming audits. Technology vendors as well support securely implementing new solutions while maintaining attestations and reporting requirements. External perspectives supplement internal knowledge for stronger defenses industry-wide.
With Threats Evolving, Vigilance Remains a Key
While sharing payment data enables commerce, related risks will persist as long as financial crime represents a lucrative endeavor. Multiple layers of security make skimming much harder, while consumer awareness short-circuits many schemes. Businesses investing in the latest tools and following directives like PCI DSS also share the responsibility to cultivate customer trust.
However, the human factor leaves room for social engineering ploys, underscoring how individual vigilance and reporting anomalies remain fundamental to containing losses industry-wide over the long run. Continuous improvement guided by data-driven strategies moreover helps stay ahead of adaptable adversaries.
Conclusion
In conclusion, skimming remains one of the top threats to financial well-being due to its damaging consequences and stealthy techniques constantly evolving with technology. However, through prudent precautions and collective action, its toll can be reduced – protecting privacy, building trust, and fostering safer digital lives for all.
Whether individual cardholders or merchants accept payments, applying basic safety fundamentals coupled with smart security practices forms a robust approach against skimming attacks. While perfect protection eludes even best-defended networks, raising the costs and difficulties for cybercriminals prevents many opportunistic breaches. Collaboration across sectors then bolsters those efforts through open information sharing, guiding research, and supporting victims.
For those looking to dive into the world of cybersecurity and stay ahead of these threats, CCS Learning Academy offers top-notch Cybersecurity courses. Our programs are designed to equip you with the skills needed to ward off cyber threats effectively. So, why not take advantage of our expertise? Enroll today, brush up on the latest techniques, and step up your defense strategy against skimming and other cybercrimes.
FAQs
In cyber security, skimming refers to the theft of card information by illegally capturing data from the magnetic stripe of a credit or debit card. This can occur through devices attached to card readers or ATMs, or via handheld skimmers used surreptitiously by dishonest employees during transactions.
Common examples include attaching skimming devices to ATMs or point-of-sale terminals that read and store all the details from a credit card’s magnetic stripe. Another example is waitstaff or retail cashiers using a portable skimmer to swipe a card separately from the legitimate transaction.
For individuals, skimming can lead to unauthorized transactions and financial loss, affecting credit scores and personal finances. For businesses, it poses risks of reputational damage, loss of customer trust, and potential financial liabilities from fraudulent charges.
Detecting skimming devices involves physical inspection of ATMs and point-of-sale terminals for any unusual attachments or modifications. For individuals, closely monitoring bank statements and account alerts can help detect unauthorized transactions early.
Prevention measures include regularly inspecting and maintaining ATMs and card readers, installing tamper-evident seals, using encrypted point-of-sale terminals, and training employees to recognize and report potential skimming devices. Consumers can protect themselves by covering the keypad while entering their PIN and using contactless payment methods when available.
Yes, technologies such as EMV (Europay, MasterCard, and Visa) chip technology make skimming more difficult because the chip creates a unique transaction code that cannot be reused. Other technologies include point-to-point encryption and tokenization, which protect card data during and after transactions.
If card skimming is suspected, individuals should immediately notify their bank or card issuer, report the suspicious activity, and request a new card. Monitoring credit reports and setting up fraud alerts can also help mitigate further unauthorized use.
Businesses can ensure compliance by adhering to the Payment Card Industry Data Security Standard (PCI DSS), which includes requirements for protecting card data, maintaining secure networks, and implementing strong access control measures.
Cybersecurity training is crucial in educating employees about the risks of skimming, how to recognize skimming devices, and the importance of securing transaction environments. Regular training ensures that staff remain vigilant and aware of the latest skimming tactics and prevention strategies.
The rise of digital wallets and contactless payments is reducing the risk of skimming as these technologies do not rely on magnetic stripe data, which is commonly targeted by skimmers. These methods use encrypted tokens and one-time codes for transactions, enhancing security and reducing opportunities for skimming.






