What is GRC in Cyber Security? Definition, Process & Benefits
- -
- Time -

Cyber threats pose one of the most significant risks to businesses today, with the global average cost of a data breach reaching $4.45 million in 2023. As cyberattacks grow more sophisticated, organizations must implement robust cybersecurity strategies to protect their data and ensure business continuity. This is where GRC (Governance, Risk management, and Compliance) comes in.
GRC provides a structured approach that aligns an organization’s cybersecurity and business objectives while managing risks and ensuring compliance. This article will explore what GRC means in the context of cybersecurity, its key components, the step-by-step GRC implementation process, and the multifaceted benefits it delivers for enhanced data protection.
Table of Contents
- Understanding GRC in Cyber Security
- The Core Principles Underpinning GRC
- The Comprehensive GRC Implementation Process
- The 6 Pillar CISA GRC Framework
- Key Benefits of CISA’s GRC Framework
- Overcoming Implementation Challenges
- Real-World Examples of Cyber GRC Success
- Best Practices for Driving GRC Success
- Conclusion
- FAQs
Understanding GRC in Cyber Security
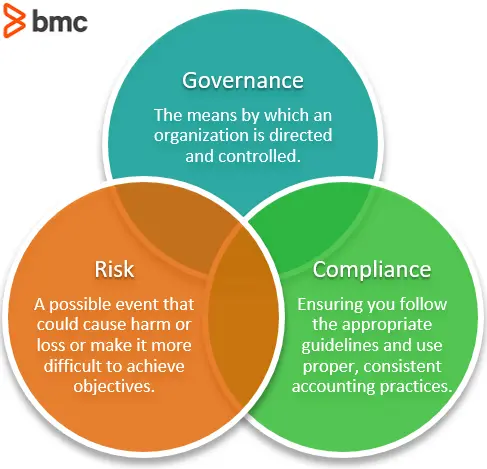
GRC stands for Governance, Risk management, and Compliance. It offers a holistic methodology designed to synchronize security efforts with business goals compliantly by integrating these three disciplines:
- Governance: Establishes accountability, corporate policies, access controls, and standard operating procedures guiding the organization’s cybersecurity vision.
- Risk Management: This entails identifying, assessing, and mitigating cyber risks that may negatively impact business operations based on severity.
- Compliance: Requires adhering to both external regulatory mandates like GDPR and internal protocols to demonstrate integrity.
Together, these pillars allow organizations to balance security with usability while optimizing technology investments.
The Core Principles Underpinning GRC
Several guiding principles characterize robust cybersecurity GRC implementations:
Executive Alignment
CISOs must receive buy-in across leadership functions like IT, finance, and legal on GRC’s value in building organizational resilience.
Risk Intelligent Culture
Staff across levels make prudent data protection choices, recognizing personal accountability for collective security.
Metrics Focused
Quantitative metrics like dwell time, malware volume, and audit results inform continuous evaluation, planning, and investment.
Adhering to these fosters proactive, disciplined security postures withstanding turbulent threat landscapes.
The Comprehensive GRC Implementation Process
Structuring cybersecurity operations on GRC requires strategic vision coupled with systematic execution spanning:
1. Define Governance Framework
Document hierarchies, data trustees, technical standards, and protocols guiding roles & responsibilities.
2. Conduct Risk Assessment
Uncover vulnerabilities and threats and quantify the potential business impact from incidents leveraging IT audits.
3. Profile Compliance Requirements
Classify essential regulatory and internal compliance needs like PCI DSS, HIPAA, and SOC2 mapping to operations.
4. Implement Controls Framework
Establish guardrails embedding security, best practices, and accountability across functions minimizing breaches.
5. Develop Actionable Policies
Frame pragmatic policies on access, encryption, testing, third parties, and responses empowering teams across levels.
6. Embed Ongoing Assessments
Institutionalize periodic control testing, audits, tabletop exercises, and continuity analysis for perpetual resilience.
This enables sound cyber risk management that is aligned with meeting business deliverables legally.
The 6 Pillar CISA GRC Framework
The Cybersecurity and Infrastructure Security Agency (CISA) has outlined a cybersecurity GRC (Governance, Risk management, and Compliance) framework encompassing six key pillars for robust implementations:
1. Risk Governance
Risk governance involves establishing accountability oversight to steer information asset-related risks. It entails setting executive-driven policies and protocols that frame how cyber risks are evaluated and addressed across units.
Effective risk governance weaves assessment processes into decision conduits at both leadership and operational levels. This embeds prudent choices that balance productive access, transparency, and security.
2. Cyber Threat Intelligence
Proactive gathering of cyber threat intelligence entails continuously tracking inputs from trusted industry sources about emerging hackers, malware variants, and exploitable vulnerabilities.
Threat intelligence feeds into anticipatory analysis of probable attack vectors and scenarios. This allows for preventing intrusions by proactively patching detectable weaknesses before adversaries exploit them.
3. Continuous Diagnostics
Persistent monitoring of organizational assets, network traffic, user activities, and access patterns enables early detection of anomalies, gaps, and risks.
Diagnostic data flows into administrative dashboards, highlighting vulnerabilities and triggering tailored interventions by security analysts to preserve integrity. The goal is perpetual vigilance through technological surveillance and human oversight.
4. Automation Integration
Workload automation integration involves orchestrating information feeds, event triggers, and responses across tools into automated workflows optimized for efficiency.
Streamlined interoperability saves costs and quickens reactions by machines executing rule-based instructions with humans supervising loop functioning.
5. Global Situational Awareness
Multi-dimensional visibility into IT environments demands integrated dashboards presenting correlated insights from across operations, including vendors, advisories, and threat bulletins.
Holistic awareness minimizes blindspots, informs trade-offs, and adapts defenses by revealing subtle shifts in business-technology risk landscapes via actionable metrics.
6. Ongoing Authorization
Regular control assessments by both internal audit and external validation entities provide ongoing authorization that policies and tools suffice relative to fluid regulatory and risk parameters.
Built-in re-evaluation workflows make compliance perpetual, not periodic, by unlinking from fixed certification calendars through continual verified security guarantees.
Together, these six pillars underpin adaptive security postures that are resilient against turbulent threat environments by weaving in continuity and coordination mechanisms across prevention, response, and recovery capabilities.
Key Benefits of CISA’s GRC Framework
The integrated governance, compliance, and cyber risk approach advocated by CISA offers multifaceted advantages:
Uniformity Across Domains
The reference architecture provides consistency in strategy spanning IT, legal, finance, and business units interfacing with shared data.
Executive Alignment
Decisions at the board level are informed by collective insights on technical and enterprise risks, ensuring leadership commitment.
Compliance Sustainability
Built-in validation controls make adhering to complex regulations reliable amidst evolving interpretations and audit expectations.
Risk-aware Culture
An ingrained focus on diagnostics and threat monitoring promotes security-centric choices by employees as a collective responsibility.
Proactive Protection
Early anomaly warnings trigger preemptive safeguards before adversaries stage complete attacks, saving costs.
Thus, CISA’s guidelines offer an invaluable starting point for organizations pursuing integrated security governance. Tailoring its tenets to specific contexts while upholding the integrative ethos is key to maximizing technology value and minimizing risk exposure.
Overcoming Implementation Challenges
Implementing GRC (Governance, Risk Management, and Compliance) is a multifaceted exercise needing coordinated efforts. However, several avoidable pitfalls can easily derail smooth execution if unaddressed. By recognizing key problem patterns upfront, practitioners can customize pragmatic solutions fitting their contexts. This enables circumventing barriers impeding effective GRC embedding.
Challenge 1: Compliance Chasing
Prioritizing compliance rule checklists over foundational security hygiene is a myopic approach to abetting breaches. Holistic data protection demands balanced investments in patching known issues, multi-factor access controls, endpoint monitoring, and log auditing alongside keeping regulatory mandates. Avoiding tunnel vision on conformance paperwork alone is vital.
Overcoming It: Integrate compliance as a component within a wider risk management repertoire. Link specific controls to key risks based on proportionality instead of merely chasing audits.
Challenge 2: Metrics Misappropriation
Metrics quantifying vulnerability cycles, malware volumes, and plan testing effectiveness can improve or hurt security posture depending on contextual interpretation. Simple data mining without perspectives guiding analytical rigor risks misleading interpretations.
Overcoming It: Embed cyber risk education across leadership levels on correctly parsing risk indicators within scenarios affecting the organization.
Challenge 3: Technology Sprawl
The burgeoning GRC solutions marketplace and promises of silver bullets perpetuate tool sprawl. But disjointed dashboards bloat security operations costs and inefficiencies without smoothing workflows.
Overcoming It: Start by inventorying existing software functionalities to avoid capability redundancies when evaluating investments. Then, integrate new solutions within predefined architectural alignments.
Challenge 4: Misplaced Prioritization
Pressures to demonstrate progress predispose security leaders to neglect minor system weaknesses lacking executive visibility. However, accumulating fragile links diminishes organizational resilience substantially over time.
Overcoming It: Maintain an ethics hotline allowing staff to report anonymous issues without fear of reprisal for overlooked gaps apart from formal channels.
Challenge 5: Expectation Mismatches
A lack of grounded understanding of transformation timelines plagues many well-intended GRC undertakings into disarray. Leaders must discern realistic Horizons spanning near-term fixes and multi-year cultural shifts.
Overcoming It: Structure execution into waves, prioritizing consequential quick wins before pursuing ambitious long poles. Maintain consistent communications on progress markers and milestones.
Sidestepping common hurdles enables smoother GRC execution:
- Balance compliance obligations with other risk reduction imperatives holistically fortifying data assets.
- Embed cyber risk training, ensuring metrics correctly inform priorities that fit scenarios.
- Consolidate software capabilities prudently, avoiding overlapping tools without security gaps.
- Welcome anonymous feedback channels revealing overlooked issues warranting consideration.
- Calibrate execution rhythms via phased pathways, allowing solid foundations before scaling.
With these insights, security leaders can charter realistic trajectories that fulfill GRC’s risk-balancing vision, which is central to robust protection. Carefully evading foreseeable obstacles unlocks frictionless journeys in the longer term.
Real-World Examples of Cyber GRC Success
While cybersecurity GRC (Governance, Risk Management, and Compliance) promises immense potential, pragmatic results often speak louder than theoretical benefits. Examining tangible transformations from leading global corporations validates GRC’s multilayered value.
Financial Services: Risk and Process Efficiency
A systematic revamp revealed vast improvements for a multinational bank despite prior robust controls. Holistic audits uncovered redundant checks and process gaps fixed within months.
Centralized visibility allowed the decommissioning of dated systems, streamlining vendor assessments, and strengthening identity protocols. Compliance overhead dropped significantly while strengthening oversight.
Healthcare: Safeguarding Data and Trust
By mapping access roles to data sensitivity, a leading managed healthcare provider refined policies lowering records theft last quarter.
Proactive de-provisioning containing recent resignations blocked unauthorized access. Patient trust dramatically improved via prompt self-disclosure and strengthening systems.
Hospitality: Securing Brand Reputation
Hospitality thrives on customer trust and loyalty, which are endangered by cyber incidents. A global hotel chain gained centralized visibility into the cyber health and risks of thousands of franchises.
Integrated dashboards rapidly alert managers of franchise anomalies allowing standardized responses minimizing brand erosion from incidents. Franchise policy education improved cyber resilience, safeguarding corporate reputation.
Technology: Optimizing Compliance Value
Despite substantial legacy investments, compliance processes consumed excessive manual effort for a leading tech provider. Updated GRC controls tracking and automated policy testing slashed audit preparation time from 49 to 11 days.
Real-time reports accelerated certification while enhancing data protection. The GRC platform delivered rapid ROI through efficiencies and risk reduction.
Key Takeaways
Together, these wins validate cyber GRC’s security and compliance optimization capabilities:
- Reduced Data Exposure: Systematic governance and revised access policies plugged data theft avenues rapidly.
- Higher Responsiveness: Centralized monitoring tools alert managers to franchise risks faster to enable support.
- Optimized Processes: Discovered redundant controls and milestones while boosting consistency.
- Bolstered Trust: Improved resilience against threats, preventing reputation erosion.
- Tangible ROI: Time and resource savings realized by automation warrant investments.
With mounting cyber risks, such GRC success stories offer blueprints for managing complex information environments. Tailoring programmatic frameworks while regularly demonstrating impact is key to thriving amid turbulence.
Best Practices for Driving GRC Success
While cybersecurity GRC (Governance, Risk Management, and Compliance) promises immense potential, pragmatic guidance can smooth transformation journeys. We distill battle-tested tips from security leaders spearheading impactful implementations.
Tip 1: Discover Your Crown Jewels
Classifying ultra-sensitive assets like intellectual property, customer data, and source code allows custom-tailoring multilayered controls to fit their criticality. Granular classification also guides access policies, encryption strengths, and business continuity plans, balancing usability with imperatives.
Tip 2: Promote Collaborative Analytics
Ingraining cross-functional analysis of threat intelligence and risk metrics preempts fragmented security views. Joint evaluation sessions to parse indicators build shared visibility, enabling cohesive responses.
Tip 3: Right Size Frameworks Contextually
The hypothesis of proportionality applies when scoping policies and controls across diverse technology and workforce groups. Rather than enforcing uniform, one-size-fits-all governance models, frame risk-calibrated guidelines aligning to access levels and impact severity.
Tip 4: Take a Phased Approach
Pace lengthy revamps via incremental building blocks proving value before organization-wide rollouts. Short-term priority quick wins maintain momentum while larger enhancements progress behind the scenes.
Tip 5: Entrench Security in Culture
Look beyond rules to influence intrinsic cultural wisdom via steady microlearning nudges ingraining secure data handling as second nature. Tiny tips over time compound, strengthening institutional resistance to negligence and emerging threats.
Thus, GRC’s meteoric rise owes much to its multi-dimensional value transcending compliance to enable robust data protection that is integral for competing globally.
Conclusion
GRC (Governance, Risk Management, and Compliance) has become an indispensable strategic imperative enabling organizations to align business goals with risk mitigation. By harmonizing policy oversight, threat awareness, and regulatory mandates, it fosters resilient cybersecurity postures that are ready for turbulent environments. Leadership commitment coupled with pragmatic execution makes or breaks GRC’s success.
Unlock your potential in cybersecurity—enroll in our CGRC – Certified in Governance, Risk and Compliance course today! Gain the skills to master governance, risk management, and compliance and propel your career to new heights. Secure your spot now and start leading with confidence.
CCS Learning Academy offers immersive cybersecurity courses guided by industry experts that equip professionals with in-demand skills. Choose from short SCM certificates to Master’s degrees to help you launch or advance your cybersecurity career.
FAQs
In cybersecurity, GRC stands for Governance, Risk Management, and Compliance. It refers to a structured approach to aligning IT with business objectives, while effectively managing risk and meeting compliance requirements.
The purpose of GRC in cybersecurity is to ensure that an organization’s IT strategies and systems are in line with its overall business goals, manage risks to its digital assets effectively, and ensure that it meets all necessary compliance regulations to protect itself and its customers.
The main components of GRC in cybersecurity include Governance, Risk Management, and Compliance. Governance ensures that IT operations align with the organization’s business goals. Risk Management identifies, assesses, and mitigates risks to minimize their impact. Compliance ensures adherence to relevant laws, regulations, and ethical standards, crucial for maintaining legal standing and avoiding penalties.
Responsibility for GRC typically lies with senior executives and the board of directors. However, implementing GRC involves collaboration across many levels of an organization including IT, security, compliance, risk management, and legal departments.
Benefits of implementing GRC in cybersecurity include enhanced decision-making, more efficient IT investments, elimination of silos, and reduced fragmentation among divisions and departments. It also helps in managing and mitigating risks more effectively and ensures compliance with laws and regulations, which can protect the organization from fines and lawsuits.
GRC provides a framework for identifying, evaluating, and managing cybersecurity risks systematically and consistently across the organization. It helps in prioritizing risks based on their potential impact and the likelihood of occurrence, ensuring that resources are allocated effectively to mitigate these risks.
Challenges include complexity of integration across different departments, the cost of GRC tools and processes, resistance to change from within the organization, and the ongoing requirement to keep up with changing regulations and security threats.
Unlike traditional security measures that may focus solely on technical defenses against threats, GRC integrates these measures into a broader framework that includes organizational governance and compliance strategies. This holistic approach ensures that security measures support business objectives and comply with regulatory requirements.
Tools used for GRC in cybersecurity include software solutions that facilitate risk assessment, compliance management, audit management, policy management, and incident management. These tools help in automating processes and providing a centralized platform for managing all GRC-related activities.
Yes, small businesses can also benefit from GRC by ensuring that they are not only protected against cybersecurity threats but are also compliant with legal and regulatory standards. This can be crucial for maintaining customer trust and avoiding penalties for non-compliance.






