Popular Topics
Introduction to Jira
ASP .NET Core
Data Analyst
MVC Web Application Development by .NET
Basic Java Programming
Introduction to Angular
Generative AI for Decision Makers
CompTIA Security+
GitHub
Tableau
.NET Secure Coding
Generative AI for Architects
Core Java Programming
CSS
ASP .Net Web Applications Development
Advance C++ 20 Programming
Tableau Server Administration
Introduction to Power BI
Real World Applications of Generative AI
Certified in Governance
CISSP
Django
Risk and Compliance
Implementing AI in Automated Enterprise
Certified in Cybersecurity Training
UX Design
XML Course
.NET Programming
Modern JavaScript
Cloud Computing
JavaScript Essentials'
Attacking and Securing C#
CompTIA Cybersecurity Analyst
CSS3
Jira
Responsive Design
Java Programming
AWS
Tableau Desktop
Applying AI for Cost Savings & Efficiency
Microsoft Office 365 Online
Cybersecurity Analyst
CISSP Exam Preparation Course
Next Level Power BI
Building a Voice Bot
Data Science and Big Data
Git
XML Learning
C++ 20 Programming
Implementing AI in Business
AI Automation Strategies
CompTIA
Administering A SQL Database
Automation with Ansible
ITIL 4 Foundation Certification Training
ITIL 4 Certification
HTM
Certified Cloud Security Professional
Penetration Testing Professional
JavaScript
SQL Data Warehouse
Advanced React
Introduction to C++
Cloud Operations on AWS
CompTIA A+ Core 2
Chief Information Security Officer
Certified Secure Software Lifecycle Professional
Kubernetes
Microsoft Azure
Voice Of Innovation
Introduction to Ansible
CompTIA IT Fundamentals
Generative AI
Network Defender
Azure AI Fundamentals
Strategic AI Dialogues
CompTIA Linux
UI/UX Design
AI Types
CompTIA Server
SQL Data Models
Introduction to GitHub
AI Principles
SQL Server Integration
Advanced Angular
AI Applications
Microsoft Power BI Data Analyst
Customer Support with AI
Mastering React
SharePoint End User
Developing AWS Services and Tools
Hadoop
CompTIA Network
React Course
Professional Development
Microsoft Azure Data Fundamentals
SQL Server Performance Tuning
Microsoft Azure Certification
Prompt Engineering for Business Users
CompTIA Cloud
SQL Server Performance Optimization
CompTIA A+ Core 1
Azure Infrastructure Solutions
Python
Azure AI Solution
Citrix
CompTIA PenTest
Citrix Cloud with Amazon Web Services
CompTIA Data+
CompTIA Cloud Essentials+
Microsoft Azure for SAP Workloads
PL-600 Power Platform Solution Architect
CompTIA Project
Azure SQL Solutions
Microsoft Azure Administrator
Microsoft Project 2016 Level 1
HTML5
Microsoft Project 2016: Level 2
Microsoft Azure Fundamentals Training Certification
Full Stack Web Development
SQL Database Infrastructure
Citrix Endpoint Management
All `Live Courses by Practice Area Courses
Test descriptionFilter by Topic
Filter by Vendor
VMware Horizon 8: Infrastructure Administration
Course Description This two-day, hands-on course gives you the skills …
What you'll learn
Identify VMware Horizon Connection Server installation, architecture and requirements
Describe the authentication and certificate options for a Horizon environment
Recognize the integration process and benefits of Workspace ONE Access and Horizon 8
Compare the remote display protocols that are available in VMware Horizon
Describe the 3D rendering options available in Horizon 8
Discuss scalability options available in Horizon 8
Describe different security options for Horizon environment
VMware Horizon 8: Deploy and Manage
Course Description: VMware Horizon 8: Deploy and Manage is a …
What you'll learn
Recognize the features and benefits of VMware Horizon
Define a use case for your virtual desktop and application infrastructure
Use vSphere to create VMs to be used as desktops for VMware Horizon
Create and optimize Windows VMs to create VMware Horizon desktops
Install and Configure Horizon Agent on a VMware Horizon desktop
Configure, manage, and entitle desktop pools of full VMs
Configure and manage the VMware Horizon Client systems and connect the client to a VMware Horizon desktop
Configure, manage, and entitle pools of instant-clone desktops
Create and use Remote Desktop Services (RDS) desktops and application pools
Monitor the VMware Horizon environment using the VMware Horizon console Dashboard and Horizon Help Desk Tool
Identify VMware Horizon Connection Server installation, architecture, and requirements
Describe the authentication and certificate options for a Horizon environment
Recognize the integration process and benefits of Workspace ONE Access and Horizon 8
Compare the remote display protocols that are available in VMware Horizon
Describe the 3D rendering options available in Horizon 8
Discuss scalability options available in Horizon 8
Describe different security options for Horizon environment
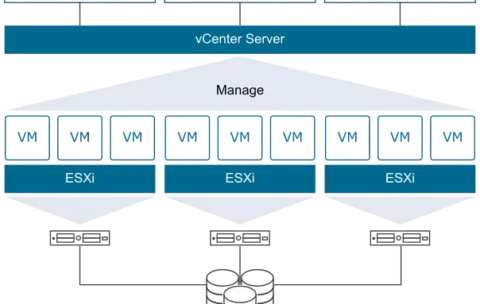
VMware vSphere: Install, Configure, Manage 7.0
Course Description This course features intensive hands-on training that focuses …
What you'll learn
Describe the software-defined data center (SDDC)
Explain the vSphere components and their function in the infrastructure
Install and configure ESXi hosts
Deploy and configure VMware vCenter® Server Appliance™
Use VMware vSphere® Client™ to manage the vCenter Server inventory and the vCenter Server configuration
Manage, monitor, back up, and protect vCenter Server Appliance
Create virtual networks with vSphere standard switches
Describe the storage technologies supported by vSphere
Configure virtual storage using iSCSI and NFS storage
Create and manage VMware vSphere® VMFS datastores
Use the vSphere Client to create virtual machines, templates, clones, and snapshots
Create a content library and deploy virtual machines from templates in the library
Manage virtual machine resource use
Migrate virtual machines with VMware vSphere® vMotion® and VMware vSphere® Storage vMotion®
Create and manage a vSphere cluster that is enabled with VMware vSphere® High Availability and VMware vSphere® Distributed Resource Scheduler™
Discuss solutions for managing the vSphere life cycle
Use VMware vSphere® Lifecycle Manager™ to perform upgrades to ESXi hosts and virtual machines
VMware vSphere: Fast Track 7.0
Course Description This five-day, intensive course takes you from introductory …
What you'll learn
• Describe the software-defined data center (SDDC)
• Explain the vSphere components and their function in the infrastructure
• Install and configure VMware ESXi™ hosts
• Deploy and configure VMware vCenter® Server Appliance™
• Use VMware vSphere® Client™ to manage the vCenter Server inventory and the vCenter Server configuration
• Manage, monitor, back up, and protect vCenter Server Appliance
• Create virtual networks with vSphere standard switches
• Describe the storage technologies supported by vSphere
• Configure virtual storage using iSCSI and NFS storage
• Create and manage VMware vSphere® VMFS datastores
• Use the vSphere Client to create virtual machines, templates, clones, and snapshots
• Create a content library and deploy virtual machines from templates in the library
• Manage virtual machine resource use and manage resource pools
• Migrate virtual machines with VMware vSphere® vMotion® and VMware vSphere® Storage vMotion®
• Create and manage a vSphere cluster that is enabled with VMware vSphere® High Availability and VMware vSphere®
Distributed Resource Scheduler™
• Create virtual networks with VMware vSphere® Distributed Switch™ and enable distributed switch features
• Discuss solutions for managing the vSphere life cycle
• Use VMware vSphere® Lifecycle Manager™ to perform upgrades to ESXi hosts and virtual machines
• Use host profiles to manage ESXi configuration compliance
• Describe how vSphere storage APIs help storage systems integrate with vSphere
• Configure and use virtual machine storage policies
CompTIA A+ Core 1
CompTIA’s A+ certification is the industry standard for validating the …
What you'll learn
Install and configure PC system unit components and peripheral devices.
Install, configure, and troubleshoot display, multimedia devices, storage devices, and internal system components.
Explain network infrastructure concepts.
Configure and troubleshoot network connections.
Implement client virtualization.
Support and troubleshoot laptops, mobile devices and print devices.
Certified Network Defender | CND
Course Description Certified Network Defender (CND) is a vendor-neutral, hands-on, …
CompTIA Cybersecurity Analyst (CySA+)
Participate in The High-Stake Cyber-Security Analyst Certification Course By participating …
What you'll learn
Assess information security risk in computing and network environments.
Analyze reconnaissance threats to computing and network environments.
Analyze attacks on computing and network environments.
Analyze post-attack techniques on computing and network environments.
Implement a vulnerability management program.
Collect cybersecurity intelligence.
Analyze data collected from security and event logs.
Perform active analysis on assets and networks.
Respond to cybersecurity incidents.
Investigate cybersecurity incidents.
Address security issues with the organization’s technology architecture.
Computer Hacking Forensic Investigator | CHFI
Course Description The Computer Hacking Forensic Investigator (CHFI) course delivers …
What you'll learn
Establish threat intelligence and key learning points to support pro-active profiling and scenario modeling
Perform anti-forensic methods detection
Perform post-intrusion analysis of electronic and digital media to determine the who, where, what, when, and how the intrusion occurred
Extract and analyze of logs from various devices like proxy, firewall, IPS, IDS, Desktop, laptop, servers, SIM tool, router, firewall, switches AD server, DHCP logs, Access Control Logs & conclude as part of investigation process.
Identify & check the possible source / incident origin.
Recover deleted files and partitions in Windows, Mac OS X, and Linux
Conduct reverse engineering for known and suspected malware files
Collect data using forensic technology methods in accordance with evidence handling procedures, including collection of hard copy and electronic documents
The computer forensic investigation process and the various legal issues involved
Evidence searching, seizing, and acquisition methodologies in a legal and forensically sound manner
Types of digital evidence, rules of evidence, digital evidence examination process, and electronic crime and digital evidence consideration by crime category
Roles of the first responder, first responder toolkit, securing and evaluating electronic crime scene, conducting preliminary interviews, documenting electronic crime scene, collecting and preserving electronic evidence, packaging and transporting electronic evidence, and reporting the crime scene
Setting up a computer forensics lab and the tools involved in it
Various file systems and how to boot a disk
Gathering volatile and non-volatile information from Windows
Data acquisition and duplication rules
Validation methods and tools required
Recovering deleted files and deleted partitions in Windows, Mac OS X, and Linux
Forensic investigation using AccessData FTK and EnCase
Steganography and its techniques
Steganalysis and image file forensics
Password cracking concepts, tools, and types of password attacks
Investigating password protected files
Types of log capturing, log management, time synchronization, and log capturing tools
Investigating logs, network traffic, wireless attacks, and web attacks
Tracking emails and investigating email crimes
Mobile forensics and mobile forensics software and hardware tools
Writing investigative reports
Dark Web Forensics and IOT Forensics