What is Reconnaissance in Cyber Security? Definition, Types & Examples
- -
- Time -

Cyber reconnaissance, also known as recon, refers to the process of gathering information about potential targets without directly interacting with them in the digital world. It is a crucial initial phase of any cyber attack carried out by threat actors to profile organizations, discover vulnerabilities, and gain valuable intelligence before attempting to breach corporate networks and systems.
Reconnaissance plays an important defensive role too as it allows security practitioners and penetration testers to think like attackers and identify security gaps from an outside-in perspective. By performing comprehensive recon, organizations can eliminate vulnerabilities and strengthen their overall cybersecurity posture.
This article provides a detailed overview of reconnaissance in cybersecurity – what it means, the various techniques used, real-world examples, and best practices to prevent such attacks. Let’s get started.
What is Cyber Reconnaissance?
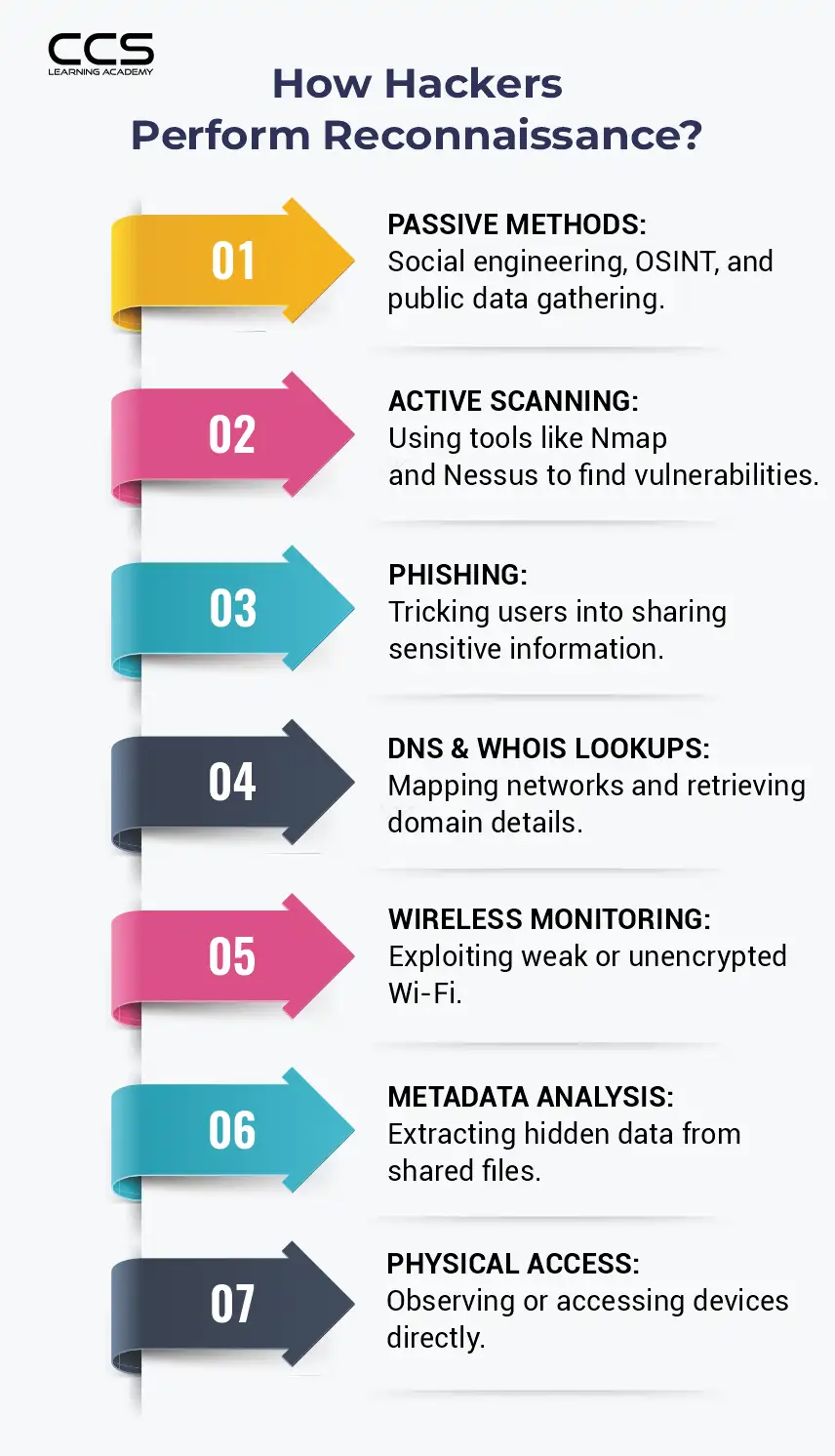
In simple terms, cyber reconnaissance refers to the process of actively or passively collecting intelligence about potential targets like individuals, organizations, networks, systems, and web applications without directly interacting with them or alerting the targets.
The goal is to conduct thorough background research and gather as much valuable information as possible including technical details, infrastructure layout, employees, business dealings, operational protocols, and more. This intelligence enables threat actors and penetration testers to accurately profile targets, understand attack surfaces, identify vulnerabilities, and carefully plan sophisticated cyber campaigns.
Some key things to note about reconnaissance in cybersecurity:
- It lays the groundwork for successful cyber attacks by providing thorough situational awareness to bad actors about their targets.
- Systematic recon allows hackers to precisely profile organizations, search for security loopholes, and effectively breach corporate infrastructure with minimum resistance.
- It is often the initial stealthy phase of a broader cyber kill-chain involving exploitation, establishing footholds, escalating privileges, and achieving objectives.
- Just like military or intelligence reconnaissance, cyber reconnaissance relies on covertly collecting and analyzing target data through both active and passive means without direct engagement or detection.
- The goal is to remain cryptic, gather maximum possible information, and create an attack blueprint before directly hitting live networks and systems.
- It plays an equally important defensive role by helping security teams think like adversaries to identify organizational blind spots and eliminate potential vulnerabilities.
So in summary, cyber reconnaissance refers to the covert intelligence gathering mission usually undertaken at the very start of a cyber attack lifecycle or a penetration test to profile targets, search for exploitable security gaps, and carefully plan the next phases of digital intrusion.
Read more: Building a Strong Cybersecurity Culture in Your Company: Tips and Strategies
Types of Cyber Reconnaissance

There are generally two main types of cyber reconnaissance techniques – active and passive. These differ based on whether they directly interact with the target systems/networks during the information collection process or not.
1. Passive Reconnaissance
Passive reconnaissance relies on openly available or intercepted data and does not require any direct engagement or interaction with target entities. The goal is to remain completely undetected while covertly profiling systems from the outside. Some common passive reconnaissance techniques include:
- Open-Source Intelligence (OSINT) Gathering: Mining publicly available information from sources like social media, websites, documentation repositories, job postings, news reports etc.
- Network Traffic Analysis: Deploying tools like Wireshark to monitor and intercept traffic flowing in and out of networks without interfering.
- Search Engine Recon: Using search engines to find technical details, port scanning reports, vulnerabilities, employee directories and more.
- Whois Lookup: Querying domain registration records to get important organization and infrastructure details.
- DNS Recon: Identifying subdomains, servers, services and other resources through DNS records.
- Social Media Monitoring: Analyzing professional and personal accounts of employees for clues.
Passive reconnaissance allows hackers to extract a rich vein of open-source data without touching live target systems. However, it may not uncover deeply hidden vulnerabilities or internal resources.
2. Active Reconnaissance
In contrast to passive techniques, active reconnaissance directly probes and interacts with target entities like networks, systems and applications in an intrusive manner. While riskier due to chances of detection, it provides more accurate internal information. Common active recon approaches include:
- Port Scanning: Sending connection requests to TCP/UDP ports to map open ports, services and firewall configurations.
- Service Enumeration: Fingerprinting services running on open ports along with names, versions and other details.
- Vulnerability Scanning: Using automated tools to actively check for known vulnerabilities in operating systems, software and configurations.
- Application Probing: Directly interacting with web apps through browsers to detect flaws like cross-site scripting (XSS), insecure direct object references etc.
- SMB/WMI Scanning: Enumerating Windows systems through Server Message Block (SMB) and Windows Management Instrumentation (WMI).
- Password Cracking: Checking password hashes or using default/brute-forced credentials to get initial access.
- Script Scans: Automating techniques through custom scripts for large-scale active reconnaissance.
Active attacks are faster and more accurate but risk tripping alarms. Recon tools often have built-in mechanisms to minimize traceability.
Read more: Is Cybersecurity A Good Career ? Pros and Cons
Reconnaissance Techniques Explained
Now that we understand the difference between active and passive reconnaissance types, let’s deep dive into some of the key intelligence gathering techniques commonly used:
1. Open-Source Intelligence (OSINT) Gathering
OSINT involves collecting openly available information about targets from public forums, social media profiles, job postings, annual reports, press releases and more without direct engagement. Some OSINT techniques include:
- Searching organizational websites for technical details, team structures, customer lists etc.
- Analyzing social media profiles of employees for clues about workplace, personal interests, vacation schedules and more.
- Mining job portfolios and resumes available online for skill sets and designations.
- Checking press releases, news archives and blog posts for announcements, events and other disclosures.
- Reviewing documentation hubs like GitHub for code snippets, configurations and design/architecture insights.
Attackers extensively leverage OSINT due to its passive nature and abundance of intelligence available in the public domain. A thorough OSINT sweep forms the cornerstone of any reconnaissance mission.
2. Network Mapping and Scanning
Mapping networks and scanning systems is one of the most common reconnaissance techniques. It helps uncover internal infrastructure details, open ports/services, vulnerable systems and potential entry points. Popular network scanning tactics include:
- Port Scanning: Sending connection requests to TCP/UDP ports to detect live hosts, open ports and services. Tools like Nmap, Masscan, etc. are widely used.
- Vulnerability Scanning: Actively checking for exploits by running vulnerability scanners like Nessus, OpenVAS, QualysGuard on targets.
- Service/Version Detection: Fingerprinting applications, operating systems and software versions responding on ports using tools like Nmap and WhatWeb.
- SMB/WMI Scanning: Leveraging Server Message Block (SMB) and Windows Management Instrumentation (WMI) to gather Windows-specific data.
- DNS Recon: Interrogating DNS records of target domains to find subdomains, servers, services and other resources. Tools like NSLookup, dig are used.
Effective network mapping allows precise targeting along with mapping out security controls – forming the foundation for subsequent exploit attempts.
3. Search Engine Reconnaissance
Search engines maintain caches and indexes of numerous documents, some of which may not even be publicly accessible anymore. Reconnaissance involves querying search engines for technical details, outdated websites, leaked documents and more using advanced operators:
- Site queries to search entire domains, e.g. site:example.com
- Filetype queries to search specific file types, e.g. filetype:pdf “internal documents”.
- Link queries to explore hyperlinks pointing towards targets, e.g. link:example.com
- Cache queries to access snapshots stored in search engine caches.
- Dork queries using logical strings to precisely query engines.
4. Vulnerability Scanning
Vulnerability scanners like Nessus and OpenVAS identify weaknesses in running services and device configurations by comparing to known vulnerabilities in databases. This allows attackers to identify exploitable gaps in the target’s defensive posture.
- Scanners probe systems and networks to detect out of date or unpatched software and firmware, misconfigurations, and other issues that could enable attacks.
- Details on which vulnerabilities exist helps attackers determine which exploits to use.
5. NetBIOS/SMB Enumeration
NETBIOS/SMB tools like Nbtstat and SMBenum collect data from the Server Message Block protocol, revealing local users, groups, shared folders and other internal resources that may not be directly exposed to the internet. This protocol is commonly used by Windows systems for network file sharing and printing. These tools reveal local users, groups, shared folders and other internal resources that may not be directly exposed to the internet.
- Usernames, group names, and shared resources can provide avenues for privilege escalation or lateral movement in a network.
- Information like this assists attackers in mapping out the network and where to search for valuable targets like domain controllers.
Read more: Top 11 High-Demand Cybersecurity Jobs Without a Degree.
6. Service Enumeration
Specific service enumeration uses techniques like SNMP scanning with tools like SNMPwalk to collect details of devices using the Simple Network Management Protocol, or LDAP scans to harvest user and organizational data from directories.
- Attributes revealed include networking configurations, installed software, and accounts.
- LDAP enumeration crawls directories like Active Directory to discover organizational units, user accounts, email addresses and more.
- Extracted information helps attackers understand the environments and find entry points.
7. Domain Analysis
Domain records can be mined for organizational insights using The Harvester, which pulls employee names, emails and subdomains from indexable sources. This intelligence supports phishing or further investigation.
It performs searches and scrapes webpages to collect employee names, email addresses, subdomains and other details. This type of intelligence supports targeted social engineering attacks or further technical investigation of discovered subdomains and accounts. The more an attacker knows about an organization and its members, the better phishing emails, phone calls or websites can be crafted.
8. Software Profiling
Identifying software versions via banners or fingerprints allows attackers to check if known vulnerabilities exist. Web server types, CMS platforms and other Internet-exposed software provide rich targeting data.
- Banners and fingerprints revealed through probes disclose what is actually running.
- CommonInternet-exposed systems like web servers, databases, content management systems all potentially have known vulnerabilities if out of date.
- With the product and version number, an attacker can search vulnerability databases to check for exploits matching their type and version. This step determines what vulnerabilities can be reliably leveraged as part of the attack plan.
9. Social Engineering
While not strictly technical in nature, social engineering plays an important role. Malicious social engineering like phishing seeks to manipulate humans into providing sensitive access or information. Reconnaissance often involves gathering organizational information to enable pretexting attempts.
Well-crafted schemes increase attack chances by circumventing technical defenses. Social profiles augment Open-Source Intelligence Collection.
- Phishing schemes aim to outsmart victims rather than technology through deception.
- Open-Source Intelligence collection across public profiles aids creating believable scenarios.
- If social engineering paves the way past an initial human target, it fundamentally changes what is possible from a technical compromise standpoint.
Read more: Top 10 Cybersecurity Certifications and Courses.
Real-world Examples
Terrorist organizations and cyber criminals both conduct cyber reconnaissance to gather intelligence and plan attacks. Terrorist groups perform reconnaissance to identify weaknesses in critical systems like infrastructure and transportation that could enable physical or cyber attacks. They conduct surveillance of these networks to map out attack surfaces and discover vulnerabilities.
Cyber criminals similarly use reconnaissance to understand potential targets before carrying out ransomware or data theft attacks. The massive 2017 Equifax data breach was preceded by months of active and passive reconnaissance by the attackers. They engaged in extensive probing and information gathering about Equifax’s network, assets, and security posture. This allowed them to precisely target the organization and steal sensitive financial data of over 147 million Americans.
Terrorists and cyber criminals leverage both passive and active techniques during reconnaissance. Passive methods involve gathering open-source intelligence without directly interacting with target systems. They may scan public databases, search engines, job sites and social media to collect employee names and roles, technical details, and other organizational data. DNS lookups and queries are also employed to map domain infrastructure without triggering defenses.
Active reconnaissance employs direct probing of targets. Malicious actors scan for open ports and services using tools like Nmap to identify potential entry points. They perform vulnerability scanning with applications such as Nessus and OpenVAS to discover known vulnerabilities that can be exploited. Network tools like ping and traceroute are used to map the network topology. Attackers also use remote access protocols and enumeration scripts to extract valuable operational data like user accounts and credentials.
Social engineering is a critical technique in reconnaissance. Terrorist groups and cyber criminals craft personalized phishing emails, text messages or phone calls to manipulate individuals into divulging sensitive access credentials or information. They gather intelligence from technical personnel at conferences or by baiting them on professional forums. All data obtained from diverse sources is then aggregated to build a comprehensive profile of the target and its security posture.
After extensive reconnaissance, malicious actors have tailored plans for compromising targets. If a vulnerable application or software version is found, they develop custom exploits. Detailed employee profiles help craft convincing phishing lures. Mapping the network aids internal spread and access to sensitive systems. With comprehensive target profiles, attacks can proceed covertly and achieve their goals before detection. Had Equifax applied strong authentication, patched vulnerabilities and segmented critical assets, the damaging data breach may have been prevented.
Best Practices to Prevent Attacks
Organizations need to take a proactive approach to security instead of just reacting to incidents.

- Regularly assessing your defenses and addressing weaknesses is crucial to thwarting attacks before they can succeed. Performing simulated penetration tests using common reconnaissance tools allows you to view your systems from an attacker’s perspective.
- Port scanning with tools like Nmap reveals open ports and services that could expose vulnerabilities if not patched. Vulnerability scanners like Nessus identify technical flaws that may be exploitable. Seeing your systems through the eyes of a hacker highlights what data they could glean from active reconnaissance. Addressing these issues takes away advantages attackers could gain in real attempts.
- SIEM solutions integrate monitoring across an organization’s entire network, applications, and user activity. They can detect unauthorized use of port scanning and enumeration utilities that may indicate internal reconnaissance or external intrusion attempts in early stages. Quickly responding to suspicious traffic patterns is important for disrupting an attack before critical assets are compromised.
- Stateful firewalls ensure only necessary approved communications can traverse networks and systems. Properly configured access controls placed on firewalls minimize what unauthorized parties can discover through exposed services and open ports. Encrypting sensitive data in transit and at rest also reduces what attackers can obtain even if initial entry points are found. Patching and software updates are a fundamental baseline for eliminating known bugs and vulnerabilities.
- Dark web sites, underground forums, and hacker chat groups should be regularly checked for any stolen passwords, credentials, or sensitive data that could impact an organization. Being aware that such information is being traded allows promptly invalidating any leaked login details or personally identifiable information that could enable account takeovers or phishing. Security teams can also glean strategic intelligence about new exploits or targeted industries to bolster defenses.
- Security awareness training and guidance educate employees about the dangers of unintentional vulnerabilities like weak passwords, susceptibility to social engineering, and dangers of connecting personal devices to corporate networks. Informed, wary employees pose difficulties for attackers relying on human factors to gain entrance. Regular refresher courses remind employees of best practices and update them on emerging new threats.
- Data encryption, access management, privacy controls, and segmentation help minimize what assailants can see even if they breach perimeter security. Encrypting transmissions and files at rest means intercepted data appears as meaningless code without decryption keys. Practicing the principles of least privilege and data minimization reduces the rewards of successful attacks.
- Investing in threat intelligence platforms and partnerships with Information Sharing and Analysis Centers (ISACs) enhances capabilities to recognize patterns. Threat intelligence solutions can identify indicators of compromise earlier, allowing preemptive action against known bad actors before valuable assets are put at risk. Collaborating with peers across sectors on identifying broad tactics, techniques and procedures used enables collective defense that safeguards entire industries.
By combining proactive network and user activity monitoring with robust access management, policy enforcement and user education; security controls form mutually reinforcing layers of defense. But defenses must evolve as attacks do with regular assessments, intelligence gathering and rapid remediation of issues uncovered. A comprehensive prevention-focused posture informed by the tactics of adversaries, protects organizations from the full lifecycle of an attack.
Read more: Are Cybersecurity Bootcamps Worth the Investment? A 2-minute Synopsis.
Conclusion
Reconnaissance is a critical phase of any cyber attack, as it enables threat actors to gather essential information about their target’s vulnerabilities and prepare a focused attack strategy. To defend against these threats, cybersecurity professionals must stay ahead of adversaries by understanding their techniques and fortifying defenses.
CCS Learning Academy offers comprehensive cybersecurity courses designed to equip you with the skills needed to identify vulnerabilities, manage risks, and implement proactive measures to secure your organization. Whether you’re just starting or advancing in your career, CCS Learning Academy provides the tools to thrive in this field.
A: Reconnaissance is the initial phase of a cyber attack, where attackers gather information about the target. This information helps them identify vulnerabilities, entry points, and valuable assets. Without proper reconnaissance, attackers are less likely to launch a successful attack, as they wouldn’t have enough intelligence on the target.
A: The two main types of reconnaissance are:
1. Active Reconnaissance: Involves directly interacting with the target system (e.g., port scanning) to gather detailed information.
2. Passive Reconnaissance: Involves gathering information without interacting directly with the target, typically through publicly available data like websites, social media, and domain information.
A: Active reconnaissance involves direct engagement with the target system, like pinging, scanning, or probing. This may alert security systems. Passive reconnaissance, however, is conducted without alerting the target, utilizing publicly available information and resources.
A: Social engineering techniques during reconnaissance involve gathering personal, professional, or organizational information from employees through phishing, pretexting, or baiting. This information helps attackers create more personalized and convincing attacks, such as spear-phishing campaigns.
A: Yes, reconnaissance can also be used for defense. Ethical hackers or security professionals use reconnaissance to identify vulnerabilities and potential attack vectors before malicious actors can exploit them. This proactive approach helps strengthen security systems.
A: Footprinting is the process of gathering as much information as possible about a target system, network, or organization. This can include domain names, IP addresses, and even employee details, providing an overall “footprint” of the target that attackers can use to plan further actions.
A: Open-source intelligence (OSINT) plays a key role in reconnaissance by leveraging publicly available data, such as social media profiles, company websites, and public records, to gather intelligence on a target. This method is often part of passive reconnaissance, minimizing risk to the attacker while still yielding valuable information.
A: By gathering information about the target system’s architecture, configurations, and software versions, reconnaissance helps attackers pinpoint potential vulnerabilities like outdated software, misconfigured firewalls, or exposed services. Identifying these weaknesses allows them to plan an attack that exploits these specific flaws.
A: Real-world examples include:
* The Equifax breach, where attackers performed reconnaissance to identify and exploit vulnerabilities in the company’s public-facing systems.
* APT (Advanced Persistent Threat) campaigns, where reconnaissance is used to gather intelligence on specific organizations before launching targeted attacks, such as data breaches or espionage.
A: Organizations can reduce the risk of reconnaissance by limiting publicly available information, enforcing strict data privacy policies, regularly auditing digital assets, using firewalls and intrusion detection systems to monitor for active reconnaissance, and educating employees about social engineering tactics.






