What is Filtering in Cyber Security? Definition, Types & Benefits
- -
- Time -

Content filtering has emerged as one of the most commonly adopted cybersecurity measures employed by organizations worldwide. As the threats to data privacy and network security continue multiplying at a rapid pace, implementing robust filtering controls has become imperative for businesses.
This article delves deep into understanding the concept of filtering, how it works, the different types, and its key benefits to cyber defenses. By the end, the reader will have a holistic perspective on this vital security technique.
What is Filtering in Cyber Security?
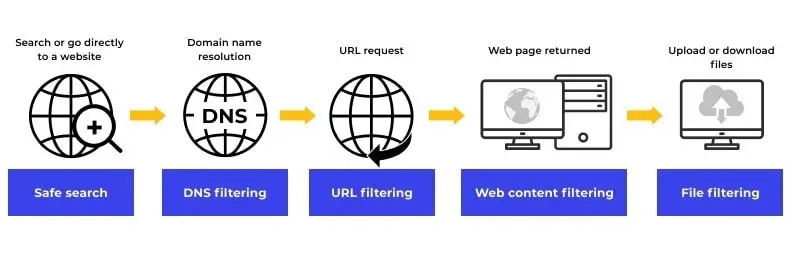
Before getting into the nitty-gritty, let’s briefly define what filtering entails in cybersecurity. In a nutshell, filtering refers to the process of screening and restricting access to certain online content, resources, or applications based on pre-defined rules and policies.
The objective is to selectively allow or block specific web entities like websites, files, emails, applications, etc., as per the security requirements and usage guidelines of an organization. Filtering acts as a preventive control at the network perimeter to cut off potentially harmful digital elements before they can enter and impact protected systems.
How Filtering in Cyber Security Works?
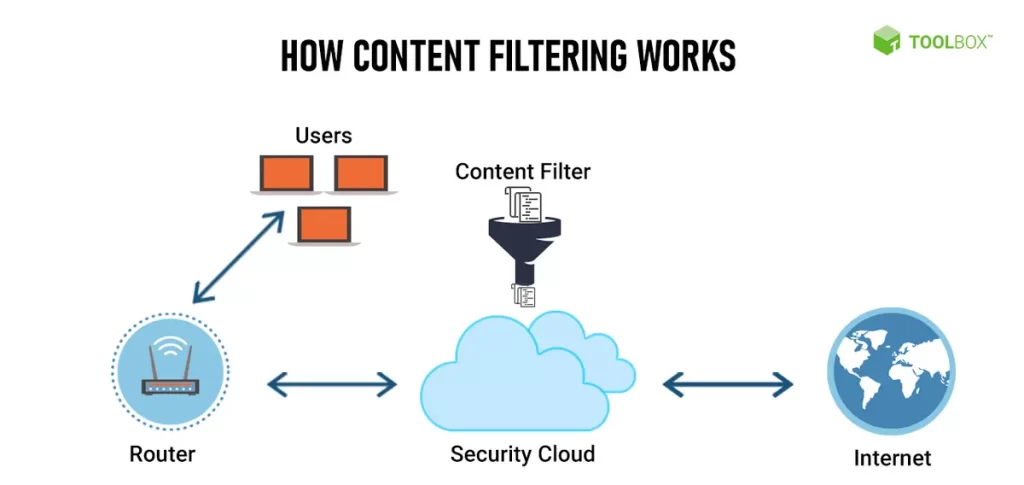
Now, let’s examine the workings of content filtering in detail:
- Software and hardware filters identify objectionable online materials by scanning for pre-defined objectionable keywords, phrases, images, etc. They maintain updated databases of these objectionable assets.
- Filters inspect and analyze incoming and outgoing web traffic in real time based on deep packet inspection techniques. They check the content transmitted against the objectionable databases.
- If a match is found, the filter either blocks the transmission or forwards it to an administrator for final review, depending on the filtering rules setup.
- Filters also support URL filtering, which examines site addresses/domains against blacklists of banned domains and allows/denies access accordingly.
- Advanced filters employ techniques like machine learning and AI to dynamically identify new threats beyond the pre-defined rule sets.
- Filtering policies can be centrally managed to apply different rules to individuals, groups, or entire departments as needed.
- Comprehensive reports on filtering events, rule violations, etc., help analyze effectiveness and enforce usage policies.
Various Types of Content Filtering
While web content filtering remains the most widely used approach, employing a multi-layered filtering strategy encompassing different types maximizes effectiveness. Let us examine the key types of content filtering in detail.
Web Content Filtering
Web content filtering forms the foundation of any comprehensive plan. It monitors and precludes access to specific websites deemed inappropriate, unproductive, or hazardous via URLs, IP addresses, or page content. This allows businesses to prevent employees from straying onto irrelevant or objectionable sites during working hours when they should be focused on their tasks.
Web filters can be configured centrally through firewalls or installed as browser extensions for granular control. They promote productivity by keeping personnel engrossed in their job roles instead of engaging in non-work-related online distractions. Additionally, web filters bolster security by impeding access to potentially malicious domains that often host malware, hack tools, or leak sensitive corporate information.
With remote and hybrid work becoming prevalent, web filtering grows increasingly vital to ensure work gets done and information stays protected regardless of location.
Email Content Filtering
Email content filtering serves as the first line of cyber defense, screening inbound and outbound messages. It scans for spam and phishing attacks and detects leakage of proprietary data or classified files through attachments. Email filters have become even more pivotal amid remote work as they fortify the perimeter regardless of where users connect from. They intercept spam and phishing emails at the gateway before users can fall prey.
Advanced filters now closely examine header details, sender credentials, and URL links embedded in messages to identify spoofing attempts with uncanny accuracy. Sophisticated attachments scrutiny uncovers Trojans and backdoors expertly hidden inside innocent-looking file types like PDFs and JPEGs. With enterprises moving their infrastructure to the cloud at a scorching pace, email filters take on added importance as the last line of protection guarding sensitive data stored in cloud applications and services.
Image and Video Content Filtering
As digital content grows increasingly visual, image and video content filtering is fast gaining prominence. They analyze multimedia files like photos and movie clips for inappropriate explicit visuals prescribed by corporate guidelines.
In an era of deepfakes and synthetic media, such filters help prevent the distribution of fabricated yet realistic imagery that can damage organizational reputation or mislead/manipulate users. They scan visual content frame-by-frame using computer vision techniques to spot nudity, graphic violence, or other prohibited content with high accuracy.
Image recognition paired with contextual understanding separates innocent photos from offensive ones. Video fingerprints allow identifying licensed content versus pirated streams. This assumes vitality for firms managing social media handles where even an inadvertent upload of unsuitable material can sour brand image and customer trust.
As immersive technologies like virtual reality gains mass adoption, image, and video filters will shape how businesses leveraging these modalities respect community standards.
Application Content Filtering
Besides web, email, and media, application content filtering puts sensible restrictions around approved and banned programs employees can access systems with. It prevents or permits certain apps, services, and network protocols based on pre-configured criteria.
For instance, file sharing, warez, and torrent applications that facilitate copyright infringement can be blocked to adhere to licensing terms. VPN users surfing anonymously raise regulatory non-compliance issues in controlled markets like China. Thus, it’s prudent to curtail personal VPN usage on work devices.
Gaming, entertainment, crypto mining, and voice/video chatting apps often cause productivity drain, which application control helps overcome. It ensures sanctioned collaboration tools only instead of unintended data leaks through unsanctioned consumer platforms. Device-level app stores offer simpler centralized procedures to define and maintain this white-list/blacklist over applications compatible with BYOD policies.
Mobile Content Filtering
As the workforce decentralizes with BYOD and corporate-owned personally enabled (COPE) devices, mobile content filtering extends the security perimeter seamlessly. Employees accessing work emails or clouds on personal mobiles/tablets require assurance proprietary data stays protected.
Mobile filters achieve this by imposing similar web access restrictions, app controls, and attachment scanning on any network sessions initiated through mobile devices. They even filter apps installed on devices regardless of how they are used – over cellular data or WiFi. GPS-based filtering granularly activates or deactivates moderation settings based on location to comply with local laws where employees may roam.
Geofencing and beacon technology enable granular geo-policies for areas like hospitals, barring sensitive content viewing on-premises. As IoT and smart environments take shape, mobile filters will dictate how connected devices access and leverage corporate services and data from distributed edge locations.
Some other types include:
- DNS filtering scrutinizes domain name query responses for malware-hosting or phishing domains to waylay associated internet traffic upfront.
- Advertisement filtering weeds out disruptive online ads that distract or occasionally promote dubious affiliate links. It fosters a safe, sanitary, and distraction-free digital experience for all.
- Device-type filtering tailors access rights and filtering severity according to whether a desktop, laptop, tablet, or smartphone is used to gain access. This is critical as the mix of personal and work devices people leverage continues to broaden.
Be it network-level filters sitting before firewall border gateways or host-based filters working on endpoint systems, choosing policies befitting business goals and obedience to industry standards and local legislation is key to the success of any content filtering deployment.
Key Benefits of Implementing Content Filtering
Implementing an effective content filtering solution provides organizations with a multitude of advantages that help strengthen network security, maximize productivity, enforce acceptable usage policies, and remain compliant with regulations. By acting as the first line of defense against malware, ransomware, phishing, and other internet-based threats, content filters play a vital role in safeguarding corporate data and systems from both internal and external risks.
Protects Network & Data Security
One of the primary benefits of content filtering is how it bolsters network and data security. The internet today is teeming with malicious actors constantly developing new techniques to infect endpoints and penetrate internal defenses. Without proper safeguards, a single click on the wrong website or download of an infected file can introduce ransomware or other malware capable of encrypting and exfiltrating valuable records.
Content filters mitigate such risks by maintaining constantly updated databases of known phishing and malware distribution sites, which are automatically blocked from being accessed. Hash lists are also used to identify specific files commonly used in attacks for scanning and restriction. This allows filters to intercept threats even before traditional security solutions like next-gen antivirus and firewalls come into play.
Enforces Acceptable Usage Policies
Aside from technical security defenses, content filtering enables efficient enforcement of acceptable usage policies that define what internet activities are and aren’t permitted during company hours. While some personal website browsing may be acceptable, many organizations have strict rules against streaming media, online shopping, gambling, and adult content, which detract staff focus and productivity at work.
Content filters parse web requests against configurable category and URL blocking lists to restrict access to such sites automatically as per defined policies. Any attempts to access barred resources are met with a block page explaining the content is prohibited under corporate guidelines. This provides an important layer of oversight to make sure company resources aren’t frittered away or misused, especially when employees may be working independently.
Improves Productivity
Being able to control internet usage has substantial benefits related to improved employee productivity throughout the workday. Numerous studies have shown how distracting sites promoting non-work pursuits like social media, news/entertainment portals, and online auctions are major productivity drainers, with people spending anything up to a few hours a day engaging with them.
By blacklisting unproductive time-wasters, content filters ensure workers devote full attention to their responsibilities rather than sporadically switching between apps and tabs. This translates to greater focus, efficiency, and output from staff, along with higher billable hours. The filtering also creates a formal divide between professional and personal internet use, which fosters a culture of accountability in the workplace.
Compliance with Regulations
In the modern business ecosystem, legal compliance with industry regulations is imperative not just for maintaining customer trust but also for avoiding costly penalties. An array of national and international laws have been established covering student and children data protection, workplace monitoring policies, data residency, and cross-border transfer rules.
Content filtering plays a key role in demonstrating conformance with these statutes. Detailed reports showcase internet usage trends, top visited domains, and potential violations of corporate AUPs to prove due diligence during audits. Pre-defined category and phrase blocking go further by allowing precision removal of information that shouldn’t be publicly available, like sensitive HR records, financial statements, etc, to avoid accidental data exposures. This eases compliance burdens significantly.
Reduces Legal Liabilities
With liability risks, content filters are invaluable in reducing legal troubles employees could otherwise fall into due to their online behaviors. While minor browsing of non-offensive sites may go unnoticed, accessing heavily illegal material brings serious repercussions.
Whether it’s viewing extremist propaganda, sexually explicit photos of minors, intimate partner violence, or any other criminal content, having corporate filters in action prevents such culpability from arising using company devices and network access in the first place. It also shields the organization from negative publicity damages in case employees are found distributing toxic, dangerous, or privacy-infringing information over official channels and files. These safeguards protect all stakeholders and maintain an ethical corporate culture.
Secures BYOD/Remote Access
For those who work remotely and bring personal devices inside environments, extending filtering controls seamlessly is critical for business today. VPN-based filtering policies capture web requests even on personal laptops and mobiles accessing organizational intranets securely over virtual private networks.
Similarly, agent-based filtering solutions integrate protections directly into home networks. This guarantees consistent oversight regardless of location to enforce policy consistency with BYOD usage as well. It also upholds security postures outside traditional office premises with devices not under centralized management otherwise vulnerable to threats. Hybrid working models find solid grounding through ubiquitous filtering that doesn’t restrict usefulness while delivering balanced safety for all connectivity scenarios.
Provides Comprehensive Reports
Actionable intelligence is key for optimizing filtering deployments and making data-driven policy changes. Comprehensive reports generated by advanced filtering platforms shine a spotlight on web usage to glean crucial insights. Interactive dashboards break down traffic stats across variables like domains, categories, devices, users, times, URLs, and more with easy-to-digest visualizations.
Numbers are supported by raw browse logs and screenshots for more context, too. Analyzing such intelligence assists in recognizing acceptable and problematic patterns to shape the next steps. It could entail white-listing specific helpful sites previously blocked by mistake or enacting tighter restrictions on non-compliant sections following violations. Report data further helps measure the ROI of content security investments by quantifying threats mitigated and time/distractions avoided.
Low Total Cost of Ownership
The total cost of ownership remains surprisingly low when factoring in complete expenses versus potential losses. While upfront licensing charges exist for browser-based and gateway filtering appliances, overall long-term value far outweighs initial outlays. Modern subscription-based pricing makes budgeting simple, with reasonable monthly user fees covering unlimited users, devices, and locations.
Easy to Deploy & Manage
Ease of adoption ranks high amongst content filtering strengths in today’s distributed workforce landscape. Cloud-centric next-gen offerings shift deployment complexity away from local infrastructures, requiring hardware procurement and extensive configuration headaches. Online administration portals facilitate centralized installation and policy orchestration from anywhere rather than needing on-premise access.
Pre-configured installation wizards, auto-updating databases, and plug-and-play integrations with major platforms simplify, bringing protections online for distributed teams with minimum effort. Further, sophisticated role-based control delegation lets administrators assign policy oversight responsibilities to regional managers while maintaining filtering consistency globally under a single MDM authority.
Future-Proof Technology
Finally, future-proofing remains a key consideration area for long-lasting technology investments. Web filtering solutions delivering perpetual value need periodic enhancement to address new threats in step with internet evolutions. Forward-thinking vendors employ large research divisions, continuously expanding category taxonomy, regular expression databases, and other risk identification capabilities based on intelligence gathered from a wide network.
Regular platform and engine updates keep solutions apace, covering emerging avenues like advanced evasion techniques, stealth cryptojacking payloads, and undisclosed website vulnerabilities leveraged by adversaries. Meanwhile, flexible licensing models accommodate the perpetual addition of locations and users as businesses scale up. This sustains security relevance and returns on filtering investments for years.
Conclusion
In conclusion, content filtering infrastructure brings multifaceted benefits that are hard to realize otherwise related to network safeguarding, productivity enhancement, policy enforcement, legal compliance simplification, liability avoidance, hybrid access handling, actionable reporting, cost-effectiveness, and manageability that justify its adoption proactively.
While initial outlays exist, the strong value proposition against large potential damages, combined with user-friendly manageability, especially for distributed teams, makes a compelling case for content security as a necessity rather than an optional investment area in today’s digital environments.
For those keen on stepping up their cybersecurity game, CCS Learning Academy’s Cybersecurity courses are an excellent resource. Our programs help you brush up on essential skills and stay ahead of emerging threats. By enrolling, you can dive into the latest security techniques, learn how to fend off potential breaches and bolster your organization’s defenses.
Don’t miss out on this opportunity to enhance your cybersecurity expertise and protect your digital assets!
FAQs
In cyber security, filtering refers to the process of allowing or blocking data packets, URLs, emails, and other forms of information based on a set of security rules. This is crucial for protecting networks and systems from malicious traffic, spam, and unwanted content.
Key types include packet filtering, URL filtering, email filtering, and content filtering. Packet filtering controls access to a network by blocking packets based on predefined rules. URL filtering restricts access to certain websites based on their URLs. Email filtering screens incoming emails for spam and phishing threats, and content filtering prevents the viewing of inappropriate or harmful material.
Packet filtering works by inspecting individual packets or small chunks of data that travel across a network. Filters are applied at network interfaces and evaluate packets to determine whether they should be forwarded or dropped, based on source and destination IP addresses, ports, and protocols.
URL filtering helps enhance security by preventing users from accessing websites that are known to distribute malware or engage in phishing attacks. It also improves productivity by blocking access to non-business related sites and helps enforce compliance with organizational internet usage policies.
Email filtering improves network security by intercepting incoming emails and analyzing them for signs of spam, phishing attacks, malware, and other security threats before they reach end-users. This reduces the risk of data breaches and helps maintain the integrity of IT infrastructure.
Content filtering in organizations plays a critical role in blocking access to inappropriate, illegal, or malicious content. It helps protect the corporate environment from security threats and maintains compliance with regulatory requirements related to internet safety and acceptable use policies.
While filtering can potentially slow down network performance due to the extra processing required, this impact is usually minimal with modern systems. Effective management includes optimizing filter rules, maintaining updated hardware, and using efficient software solutions that minimize latency and maximize throughput.
Challenges include maintaining an up-to-date filtering database, managing false positives and negatives in filtering processes, and ensuring that filtering measures do not overly restrict legitimate business activities. Regular reviews and updates of filtering policies are essential to address these challenges.
Filtering helps organizations comply with data protection regulations by preventing the leakage of sensitive information and blocking harmful or illegal content. It supports compliance with standards such as GDPR, HIPAA, and others that require protection of data from unauthorized access.
Future developments may include more sophisticated artificial intelligence (AI) and machine learning (ML) algorithms to enhance the accuracy of filtering mechanisms. These advancements are expected to improve the detection of complex threats and reduce false positives, making filtering more effective and adaptive to emerging security challenges.






