What is MDR in Cyber Security? Definition, Features & Benefits
- -
- Time -

Cyber threats are growing more advanced, persistent, and devastating in impact. Attacks are increasing in frequency, complexity, and cost. A 2022 IBM report states that the average cost of a data breach has risen to $4.35 million.
Such a landscape calls for advanced security capabilities, enabling rapid detection and response. This is leading more enterprises to explore managed detection and response (MDR) services. Gartner predicts that 50% of organizations will adopt MDR services by 2025, highlighting the immense value proposition.
This comprehensive guide will equip you with in-depth knowledge of MDR in cybersecurity. We’ll explore:
What is MDR?
- How does MDR work?
- MDR features
- MDR benefits
- MDR challenges
- MDR vs. other services
- Choosing an MDR provider
Let’s get started.
Table of Contents
- What is Managed Detection and Response?
- How Does MDR Work?
- Critical Capabilities of MDR in Cybersecurity
- Bolstering Tools with Human Expertise
- Benefits of Adopting MDR
- MDR vs. Other Cyber Security Approaches
- Choosing an MDR Provider
- Real-World Examples of MDR Cybersecurity Success
- Essential Facts on MDR in Cybersecurity
- Concluding Thoughts on MDR in Cybersecurity
- FAQs
What is Managed Detection and Response?
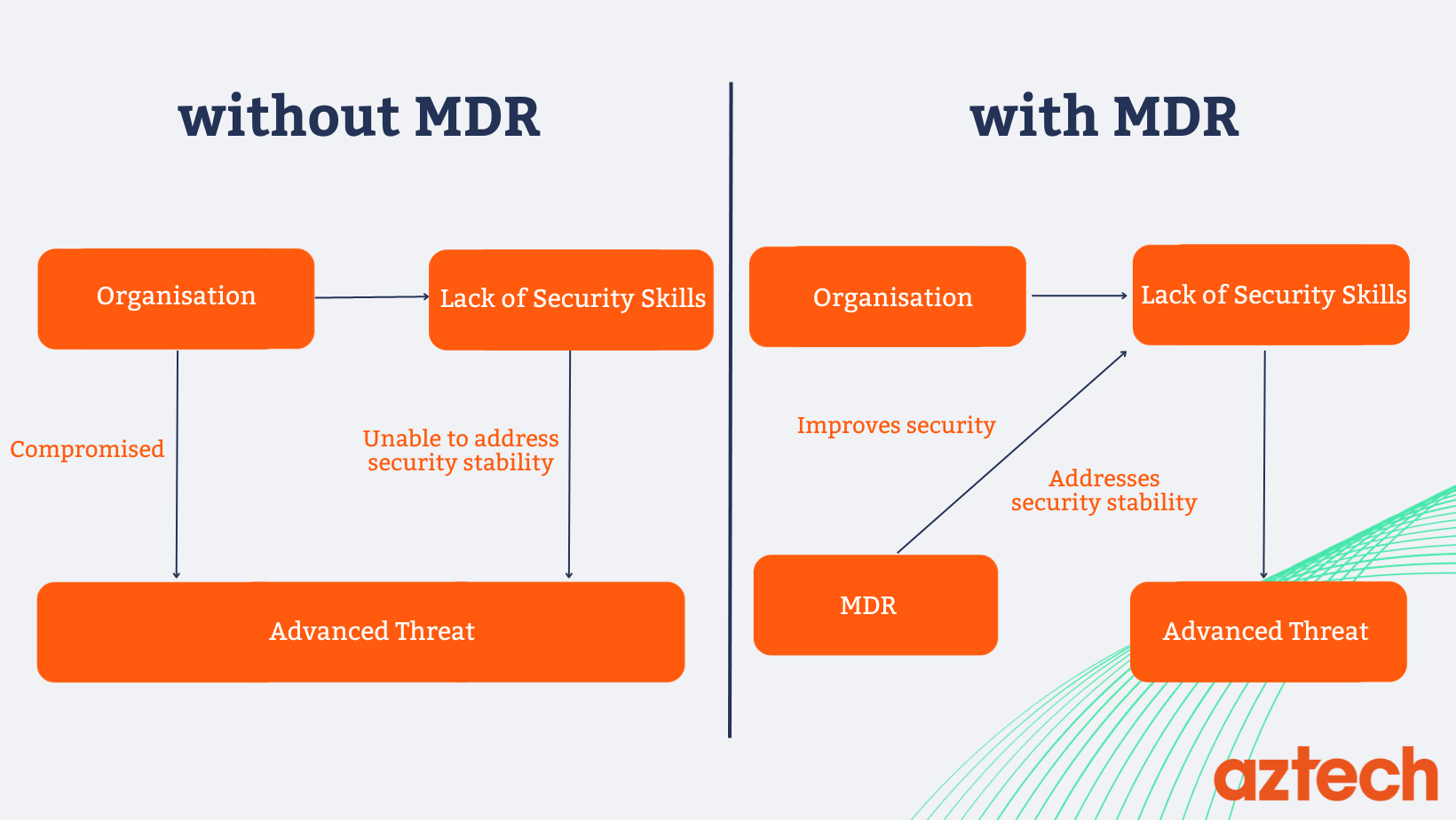
Managed detection and response (MDR) offers a critical security capability through predictive threat monitoring, swift incident response, and expert remediation. MDR providers supply trained cybersecurity experts along with advanced analytics to continuously safeguard critical assets.
More specifically, MDR services entail Six Key Capabilities:
Asset Discovery & Visibility
MDR tools provide complete visibility by automatically discovering IT assets across cloud, on-prem, and hybrid environments. Comprehensive insights help prioritize protection for crown jewels.
24/7 Threat Monitoring
Sophisticated analytics augmented by cyber experts hunt continuously for IOCs spanning endpoints, networks, emails, identities, and the cloud. The team screens torrents of security signals to pinpoint genuine threats.
Alert Triaging & Analysis
Integrated engines rapidly correlate cross-domain indicators while analysts enrich context, separating priority threats from noise. Targeted recommendations guide optimal response.
Incident Response
Specialized incident response teams swiftly contain confirmed threats through proven playbooks while investigating
scope, objectives, and recovery needs.
Guided Remediation
Step-by-step instructions lead IT teams to eliminate footholds, restore configurations, and harden defenses during recovery via phone, email, or portal.
Compliance Assistance
Experts help collect forensic data, document response steps, and ensure mandated disclosures to demonstrate due diligence. Custom reports detail mitigation policies and procedures.
Together, these six pillars of MDR offer organizations a force multiplier upholding cyber resilience. Next, let’s explore how MDR capabilities function.
How Does MDR Work?
MDR capabilities seamlessly unify people, processes, and technology to facilitate end-to-end threat lifecycle management across four key phases:
Data Collection
The starting point for impactful MDR is gathering comprehensive data. Endpoints, networks, cloud accounts, and custom apps are monitored to supply rich telemetry that powers subsequent analyses.
Continuous Monitoring
Sophisticated correlation engines screen the deluge of signals using behavioral models and anomaly detection techniques hunting for threats. Priority alerts are escalated to analysts for urgent inspection.
Threat Analysis
Cyber experts adept at intrusion techniques analyze alerts leveraging threat intelligence to determine the sincerity of alerts. Novel attacks undergo deep investigation to reveal impact, objectives, and entry points.
Incident Response
Confirmed incidents initiate containment by skilled personnel to isolate threats and advise recovery procedures aligned to business risk. Forensics help identify gaps permitting compromise.
This full spectrum coverage from noisy signals to verified incidents allows smoothly balancing automation with human diligence to accelerate threat neutralization.
Now that we’ve reviewed the MDR concept, let’s analyze key components in greater depth.
Critical Capabilities of MDR in Cybersecurity
MDR distinguishes itself from other managed security services through six essential capabilities:
Continuous Endpoint Monitoring
Endpoints represent a prime attack vector due to their ubiquity and frequently outdated safeguards. MDR continuously audits laptops, servers, and IoT devices via installed agents to detect intrusions, misconfigurations, and exploitation attempts.
Network Traffic Analysis
By inspecting network packets and metadata for suspicious patterns, MDR can reveal command and control communications, internal reconnaissance, and data exfiltration undertakings that signature-based tools miss.
Email Security
Spear phishing emails represent one of the top infection vectors. MDR screens inbound emails, attachments, and URLs for malware and impersonation red flags that can dupe recipients and trigger infections.
Cloud Infrastructure Entitlements
MDR tools automatically inventory cloud resources, workloads, and entitlements, assessing permissions and data flows to expose risky over-privileging, third-party data sharing, and compliance gaps before adversaries exploit them.
Identity Governance
Continuously tracking identity and access patterns helps discern compromised credentials, unauthorized data access, and privilege escalation attacks across hybrid environments.
Security Orchestration & Automation
Playbooks codifying incident response procedures based on MITRE ATT&CK techniques accelerate containment of confirmed threats while machine learning models bolster threat hunting.
Unifying insights across these lenses fuels precise threat detection tailored to each organization’s terrain. However, technology alone is incomplete without the right experts to realize MDR’s promise.
Bolstering Tools with Human Expertise
While correlation engines and AI models accelerate aspects of analysis, cybersecurity still necessitates specialized human intuition. MDR providers field experienced teams covering:
Incident Responders
Swiftly isolating confirmed threats requires strategic insight into adversary tradecraft. Responders suggest containment measures recognizing complications of business-critical assets.
Malware Analysts
Inspecting advanced code and evasion tactics allows precise identification of embedded payloads, trigger conditions, and lateral movement techniques crucial for recovery.
Forensic Investigators
Reconstructing full breach timelines post-mortem guides strengthening defenses and compliance reporting. Threat hunters proactively seek out subtle indicators of active threats.
Cloud Architects
Inventorying cloud resources correctly while tracking suspicious entitlement changes demands a grasp of intricate hosting environments and access governance protocols.
Compliance Specialists
Satisfying regulatory mandates around incident notification, data preservation, and response documentation necessitates dedicated expertise in mapping controls to protocols.
This multilayered human support empowers accurate verdicts on ambiguous alerts while advising techniques benefiting unique environments. Augmenting tools with human insight is the hallmark of robust MDR. Now, let’s examine the business impact of MDR adoption.
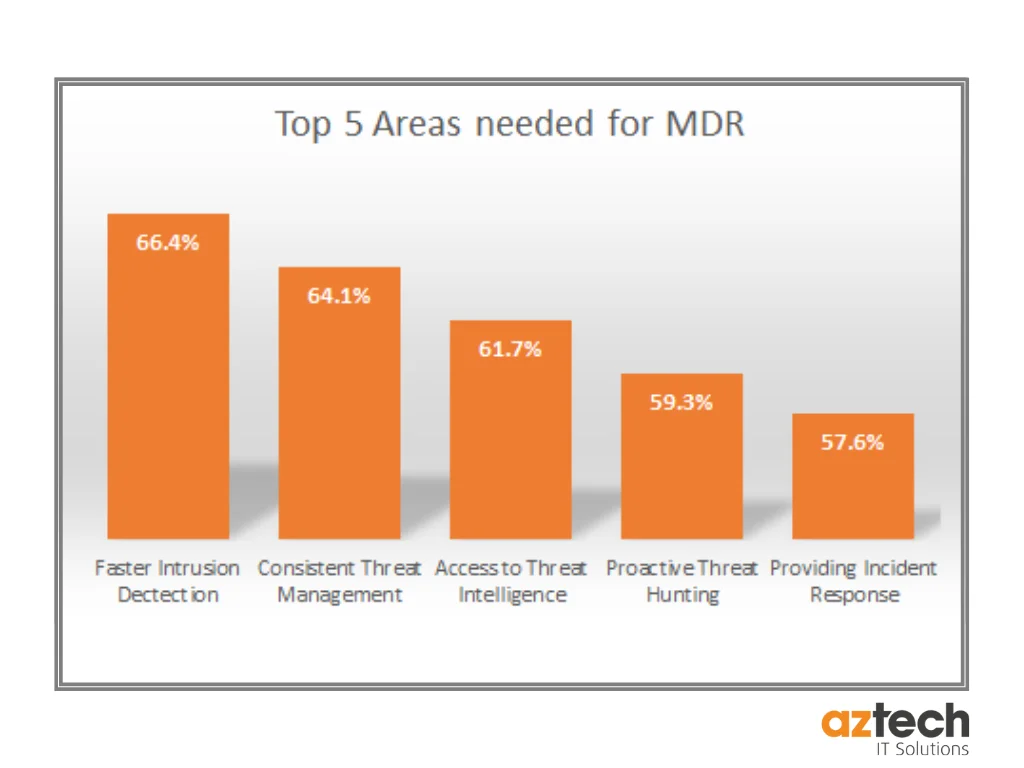
Benefits of Adopting MDR
Myriad advantages explain the surging interest in MDR services. The top five business benefits include:
Improved Threat Detection
Most breaches transpire months before eventual discovery, allowing adversaries to entrench themselves deeply. MDR experts are adept at subtle signs of attack and shrink this window to minutes, supplying precious time to contain the damage.
Accelerated Incident Response
Guided playbooks honed across incidents effectively isolate threats recognized by the team while hardening through lessons learned managing sophisticated attacks.
Reduced Alert Fatigue
Ongoing noise filtering and dedicated triaging resources save frontline staff from burnout and grappling with thousands of benign daily alerts across siloed tools.
Superior Use Of Tools
Optimizing configurations and upgrading EDR capabilities based on findings allows buoying detection strengths while patching blindspots.
Scalable Coverage
24/7 availability of seasoned specialists parallelizes response choreography, surmounting thin IT team challenges and tackling complex threats single-handedly.
Derivatives like MDR for endpoints (MDE) and network (MDN) enable tailoring services to capability gaps preventing one-size-fits-all approaches. Now that we’ve detailed key benefits, let’s contrast MDR with related alternatives.
MDR vs. Other Cyber Security Approaches
Given MDR’s rising popularity, how does it contrast with related services like MSSP or SOCaaS? What distinguishes modern MDR? Let’s clarify key nuances.
MDR vs. MSSP
- MSSPs focus more on compliance-centric services like audits, policy reviews, and technology maintenance rather than advanced threat response, which MDR specializes in.
- While MSSPs monitor known threats and generic anomalies, MDRs leverage specialized threat hunters to seek out sophisticated attacks.
- MSSP services lack hands-on response and recovery coordination capabilities that are central to MDR.
MDR vs. SOCaaS
- SOCaaS delivers software that integrates threat intel feeds, analytics dashboards, and ticket queues without human participation. MDR backs tools with seasoned response personnel.
- Machine learning in SOCaaS can only screen events for predefined characteristics, unlike adaptive human analysis, which is applied by MDR teams.
- SOCaaS users are expected to interpret alerts, hunt threats, and remediate incidents themselves, unlike guided support received from MDRs.
MDR vs. In-House SOCs
- Skilled cybersecurity talent is scarce and expensive to hire full-time, prompting MDR’s outsourced on-demand model.
- Around-the-clock in-house SOC staffing commonly suffers from undermanned night shifts, unlike MDR’s persistent 24/7 vigilance.
- Duplicate tooling, retention issues, and training overheads make internally duplicating MDR capabilities cost-prohibitive for most firms
Positioning the MDR suite adjacent to SOAR, SIEM, and XDR rather than as a replacement unlocks combinatorial strengths benefiting risk-conscious leaders.
Now that we’ve clarified how MDR contrasts with supplementary options, what factors guide provider selection?
Choosing an MDR Provider
Myriad MDR services exist today with bespoke delivery models and toolsets warranting judicious vetting tuning offerings to internal environments and aptitudes.
Coverage Alignment
Balance endpoint visibility against network traffic inspection capacities based on attack surface complexity since few offer both. Cloud workload and identity governance support are must-haves for contemporary terrain.
Analytics Sophistication
Evaluate threat detection efficacy beyond signatures to include behavioral techniques like lateral movement pattern recognition, which is vital to countering advanced enemies. False positive management is equally key to usable services.
Suitable Pricing Approach
Steer away from rigid long-term contracts, allowing flexibility to pivot as needs evolve. However, ensure assistance levels and policy tuning support map clearly to billed tiers without surprises.
Incident Response Rigor
Assess forensic investigation and threat containment previously demonstrated on sizable breaches for meticulousness begetting air-tight cases and water-tight recovery.
Compliance Assistance Range
Cross-check sensitive regulatory regimes like HIPAA and PCI DSS for satisfactory control support, often requiring niche diligence during chaotic times.
While vetting technology lends equal weight to assessing personnel experience confronting complex assaults at client sites, cementing trust in staff competencies. With a multitude of specialty MDR flavors maturing, both capability scope and scrutinization are pivotal to fruitful adoption able to best waist-high threats.
Real-World Examples of MDR Cybersecurity Success
Beyond features, what tangible transformations have MDR realization fueled across industries? Let’s examine 4 compelling snapshots.
Financial Institution
Problem: Increasingly sophisticated phishing luring staff to open embed executables evaded legacy AV, letting ransomware encrypt 3200 Windows endpoints.
Solution: MDE with AI-augmented threat hunting recognizing related anomalies limited infection to 500 nodes by alerting 2 hours post-phishing. MDR experts contained damage through isolation, saving 48 hours via guided remediation, preventing business disruption.
Healthcare Provider
Problem: Supply chain attack piggybacked malicious code through vendor patch management system for accessing patient records over 6 months.
Solution: Holistic network-endpoint dynamic analytics spotted unusual internal traffic from the vendor server, triggering expert investigation revealing the breach. MDR assisted in filing an HHS breach notice after safely quarantining exfiltrated records through recommended actions.
Technology Manufacturer
Problem: Spyware-laden patents submission portal lets attackers sneakily monitor R&D activities by jumping to partner portals via federated access.
Solution: MDR cloud entitlement reviews suspiciously flagged new app submission scripts prompting app teardown, exposing backdoor access, and adding malware scanners to foil the plot.
Retail Corporation
Problem: Compromised admin credentials purchased from the dark web allowed the installation of POS malware to scrape tens of thousands of payment cards over Black Friday weekend.
Solution: Identity-based MDR behavior analysis spotted simultaneous foreign VPN logins notifying ops who reset admin credentials containing damage while MDR advised patching by assessing impacted applications.
While details vary, the common thread is transformational risk reduction from strategic MDR adoption, navigating each situation.
Essential Facts on MDR in Cybersecurity
MDR empowers security teams to modernize threat management with services strategically balancing in-house skills. Core concepts to recall about MDR include:
- MDR enhances security operations through managed threat hunting, swift incident response, and recovery oversight.
- Continuous endpoint, network, and cloud visibility coupled with expert human judgment spur threat containment at machine speed.
- Mature MDR capabilities diverge from MSSPs and SOCaaS by emphasizing hands-on response support led by seasoned specialists.
- Choosing MDR partners entails verifying efficacy on metrics like detection accuracy, recovery assistance range, and compliance adequacy, befitting organizational requirements.
With cyber risk magnifying amid proliferating attack vectors, MDR’s active vigilance paradigm can mean the difference between rapid resilience and prolonged pandemonium. As Gartner predicts, over 50% of enterprises will adopt these services by 2025; learning to wield MDR capabilities offers boards, CEOs, and security leaders a pivotal opportunity to architect durable defenses, enriching security maturity.
Concluding Thoughts on MDR in Cybersecurity
As cyber threats grow more frequent and sophisticated, managed detection and response (MDR) has solidified its position as a vital component of modern security strategies. By combining specialized tools with human expertise, MDR empowers organizations to proactively strengthen defenses and rapidly respond to emerging attacks.
Core tenets to remember about MDR include its emphasis on threat hunting, swift incident response, and recovery oversight fueled by security analysts and engineers working 24/7. MDR solutions enhance visibility and allow stretched security teams to focus their energies on priorities rather than being bogged down in repetitive tasks.
With cyber risks only set to intensify going forward, evaluating MDR partners allows security leaders to strategically uplift monitoring and response capacities, calming turbulent times.
CCS Learning Academy offers immersive cybersecurity training guided by seasoned practitioners to fast-track careers. Choose from short-term SCM certificates to Master’s programs spanning cloud security, risk management, and incident response tailored to varied experience levels. Graduates walk away with in-demand technical expertise along with resume-enhancing certifications to unlock new roles and higher salaries. Invest in future-proof cyber skills with CCS Learning Academy today!
FAQs
MDR stands for Managed Detection and Response. It is a cybersecurity service that provides organizations with threat-hunting, monitoring, and response solutions. MDR is designed to rapidly identify and mitigate threats without the need for significant in-house security expertise.
Unlike traditional cybersecurity services that often focus on preventative measures and infrastructure management, MDR is actively engaged in detecting, responding to, and mitigating cyber threats in real time. MDR services use a combination of technology, automation, and human expertise to provide a more dynamic and proactive approach to security threats.
Key features of MDR include 24/7 monitoring and alert management, advanced threat detection capabilities using AI and machine learning, incident response and remediation, and continuous system and network assessments. These services are typically delivered through a combination of proprietary technologies and expert security analysts.
Organizations of all sizes that may not have the resources to develop and maintain a full-scale, in-house IT security team can benefit from MDR services. MDR is particularly beneficial for small to medium-sized enterprises that require robust cybersecurity protection but may lack the expertise or budget to manage it internally.
Benefits of using MDR services include enhanced detection of advanced threats, reduced response time to incidents, access to cybersecurity expertise, and improved compliance with data protection regulations. MDR services also help in reducing the overall operational costs associated with managing and responding to cyber threats.
MDR services use a variety of advanced technologies and techniques, including behavioral analytics, threat intelligence, anomaly detection, and machine learning algorithms. These tools help in identifying unusual activities that could indicate a security threat, providing early detection of potential breaches.
The response process in MDR typically involves containing the threat, eradicating the root cause of the attack, recovering the affected systems, and conducting a post-incident analysis to prevent future incidents. MDR providers often take actions remotely and coordinate closely with the client’s internal IT team.
MDR is not typically a replacement for an existing IT security team but rather a complement to enhance an organization’s cybersecurity capabilities. It provides specialized expertise and tools that may be beyond the scope of a traditional IT security team, especially in areas like real-time threat intelligence and incident response.
Organizations should consider the provider’s expertise, the technology stack they use, their approach to threat detection and response, compliance with industry standards, and their ability to integrate with existing security systems. Reviews and testimonials from current clients can also provide insights into the provider’s effectiveness and reliability.
MDR significantly enhances an organization’s cybersecurity posture by ensuring continuous monitoring and immediate response to security threats. This proactive approach helps in minimizing the potential impact of cyber-attacks, maintaining business continuity, and protecting sensitive data from breaches.






